Forgot your Android password? I get it - we've all been there, staring at our own phone like it's suddenly become a stranger. The good news? You might not need to factory reset. The bad news? Your options are pretty limited, especially if you have a newer phone.
Let me be straight with you: most "miracle" unlock methods you'll find online either don't work anymore or require setup you probably didn't do beforehand. But there are still a few legitimate ways to get back in without losing your data.
Professional unlock solutions now support over 20,000+ Android phone and tablet models, including Samsung, Xiaomi, OPPO, and other major manufacturers with Android version 5 and above. The challenge is finding what actually works for your specific device without falling for outdated advice.
Table of Contents
The Reality Check You Need First
Google's Built-In Recovery Methods (Your Best Bet)
Technical Methods That Might Work
Commercial Software Solutions
Physical Tricks Worth Trying
Why Modern Phones Are So Hard to Crack
Prevention for Next Time
When to Accept the Factory Reset
The Reality Check You Need First
Before we dive into methods, here's what you need to know:
Google's Find My Device works great - if you set it up beforehand
ADB methods only work if you previously enabled USB debugging (most people haven't)
Commercial unlock tools work better on phones from 2019 and earlier
Modern Android security makes bypass attempts incredibly difficult
Emergency call exploits mostly died with newer Android updates
Pattern locks are slightly easier to crack than PINs or passwords
Prevention beats recovery every single time
Recent security updates have made Google's Find My Device even more powerful. The service now allows users to factory reset devices remotely when traditional unlock methods fail, though this feature requires proactive setup to be effective.

Google's Built-In Recovery Methods (Your Best Bet)
Google actually wants you back in your phone, which is refreshing. Their recovery methods are your best shot at avoiding a factory reset, but they only work if you were smart enough to set them up beforehand.
When dealing with locked devices, having a reliable protective case becomes crucial for maintaining device integrity during recovery attempts. Our most protective phone cases ensure your Android device stays secure throughout the unlock process.
Google Recovery Method |
What You Need |
Success Rate |
Data Loss Risk |
|---|---|---|---|
Find My Device |
Google account logged in, location enabled |
High |
None |
Smart Lock - Trusted Places |
Pre-configured locations |
Medium |
None |
Smart Lock - Trusted Devices |
Bluetooth devices paired |
Medium |
None |
Smart Lock - On-body Detection |
Feature enabled beforehand |
Low |
None |
Find My Device - Your Digital Lifeline
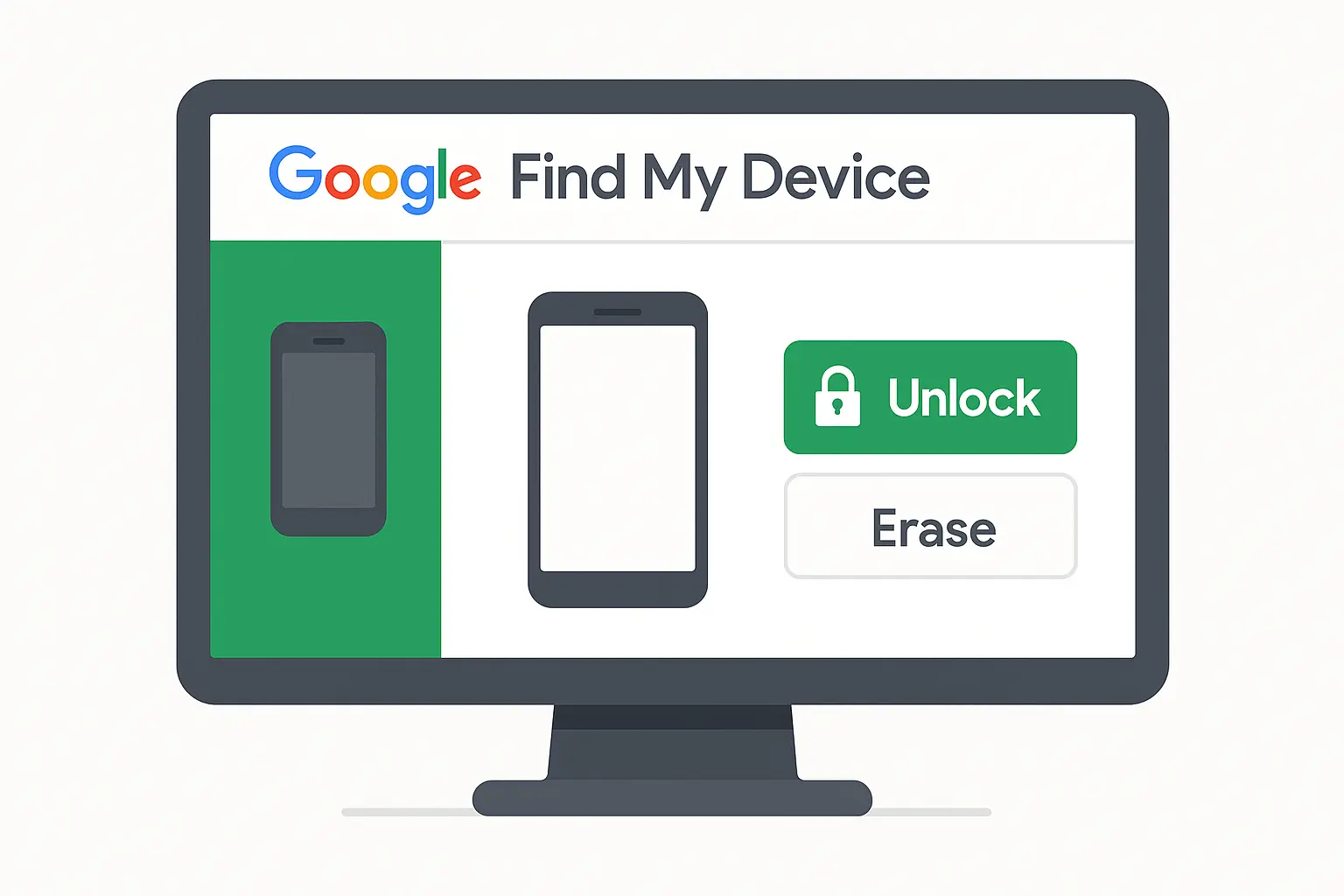
This is your golden ticket if you set it up. Find My Device can remotely unlock your Android phone through any web browser, but your device needs to be signed into your Google account with location services enabled and connected to the internet.
Here's how it works: log into your Google account from any computer, select your locked device, and choose the unlock option. Sarah forgot her Galaxy S21 PIN after switching from a pattern lock. Since her phone was connected to WiFi and logged into her Google account, she accessed Find My Device from her laptop, selected her phone, chose "Lock" to set a temporary password, then used that temporary password to get back in and reset her original PIN.
Smart Lock - The Backdoors That Save You
Smart Lock features create legitimate backdoors that can save your bacon. Trusted locations keep your phone unlocked at home or work, trusted devices maintain access through Bluetooth connections, and biometric recognition might still work even when the password system is acting up.
These aren't foolproof, but they're worth trying before more drastic measures. I've seen people get back into their phones simply because they forgot their smartwatch was connected as a trusted device.
Smart Lock features to check:
Trusted places (home, work, frequently visited locations)
Trusted devices (smartwatch, car Bluetooth, earbuds)
On-body detection for pocket/hand recognition
Voice Match for "OK Google" commands
Face recognition (if it's working properly)
Technical Methods That Might Work
Let's talk about ADB - the method every tech forum swears by. Here's the reality: it only works if you already enabled USB debugging in developer options. And honestly, most people have never even heard of developer options, let alone turned on USB debugging.
Professional unlock tools often require multiple connection attempts, making durable charging cables essential. Consider investing in high-quality phone chargers that won't fail during critical unlock procedures.
ADB Commands - For the Tech-Savvy
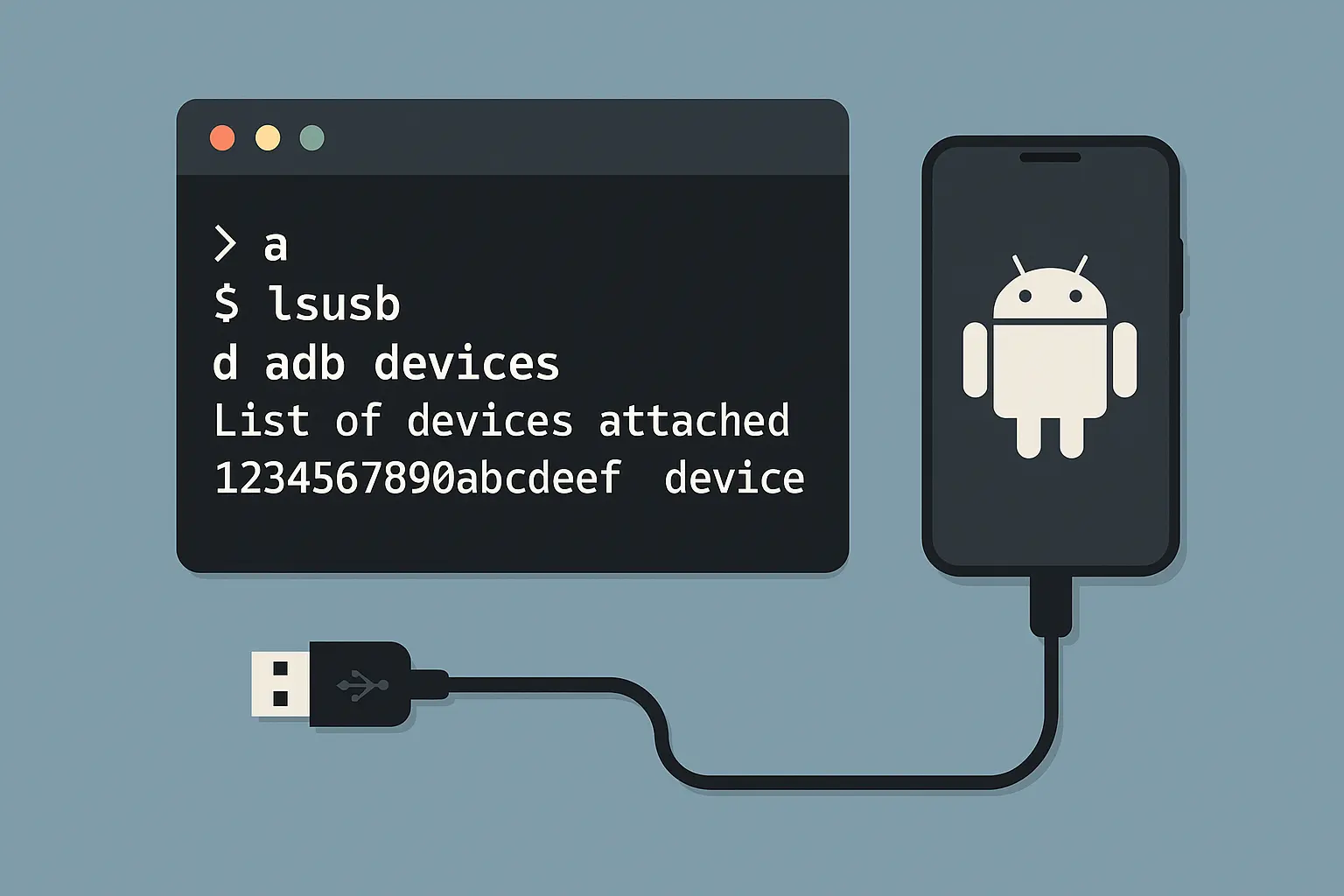
If you're one of the rare folks who enabled USB debugging, you might get lucky. ADB can sometimes delete the files that store your password, but it's gotten much harder with newer Android versions. I've seen people spend entire weekends trying ADB commands that worked great in 2018 but do absolutely nothing now.
What you need for ADB to even have a chance:
USB debugging already enabled (dealbreaker for most people)
Proper drivers installed on your computer
An actual data cable, not just a charging cable
Your phone to trust your computer (which you probably never set up)
The most common ADB approach tries to delete files like gesture.key or password.key from your phone's system. Tech enthusiast Mike successfully used ADB commands to remove his Pixel 3's pattern lock by deleting the gesture.key file. After connecting via USB, he entered "adb shell rm /data/system/gesture.key" and rebooted, which cleared the pattern requirement. However, this method failed on his newer Pixel 6 due to enhanced security protections.
Database Modification Techniques
Advanced users can try accessing Android's password database files directly through ADB. This involves connecting your device to a computer, navigating the Android file system through command-line interfaces, and locating password hash files in the system partition.
Modern Android versions make this incredibly difficult by requiring root access or bootloader unlocking. The reality? Most modern devices have patched these vulnerabilities, making file removal commands more of a Hail Mary than a reliable solution.
According to user success reports, ADB file removal methods work on approximately 5 failed unlock attempts before triggering the "Try again in 30 seconds" message, after which users can access the "Forgot Pattern" option on Android 4.4 and lower devices.
Commercial Software Solutions
Commercial unlock tools love to promise they can crack any phone. The marketing makes it sound easy - just plug in your phone and click a button. Reality check: these tools work best on phones from 2019 and earlier.
Dr.Fone, DroidKit, and similar programs do work sometimes, but they're expensive and their success rates have dropped significantly. They're basically racing against Google's security updates, and Google is winning.
Unlock Tool |
Price Range |
Supported Devices |
Android Version Compatibility |
Success Rate |
|---|---|---|---|---|
DroidKit |
$60+ |
20,000+ models |
Android 5.0+ |
High (older devices) |
Dr.Fone |
$70+ |
Samsung, LG, HTC |
Android 6.0 and below |
Medium |
Android Unlock |
$50+ |
Most major brands |
Android 4.4-9.0 |
Medium |
iSkysoft |
$65+ |
Limited selection |
Android 4.0-8.0 |
Low |
The honest breakdown:
They cost $50-100+
Work better on Samsung and LG phones
Almost useless on phones running Android 11+
Often require factory reset anyway for newer devices
I've watched friends pay for these tools only to discover their Pixel 6 or Galaxy S22 isn't supported for data-preserving unlocks. The companies are usually good about refunds, but it's still frustrating.
Recent developments in commercial unlock tools show improved compatibility with Samsung devices. Tools like DroidKit now support Galaxy S22, S21, and S10 series without requiring root access, though they still require factory reset for data erasure.
Open Source Alternatives
Free, community-developed tools combine multiple bypass methods but require more technical knowledge and carry additional risks. These solutions often use fastboot commands and custom recovery modes, though they typically require bootloader unlocking (which triggers factory resets on most modern devices).
Developer Jake created a custom script combining multiple ADB commands to unlock his OnePlus 7 Pro. The script attempted pattern file deletion, then PIN removal, and finally fell back to bootloader unlock commands. While successful, the process took 3 hours and required extensive Android development knowledge that most users lack.
Physical Tricks Worth Trying
Remember those cool emergency call hacks from YouTube? Yeah, Google patched most of those years ago. But if you've got an older phone, they're worth trying before you give up.

Emergency Call Exploits
The old emergency dialer exploit used to let you access the camera during an emergency call, then navigate to settings. It was pretty clever, but it only worked on Android 6 and below.
Older Android versions contained vulnerabilities in emergency dialers that clever users could exploit for system access. Camera access during emergency calls sometimes led to gallery access and eventually system settings, while contact navigation from emergency interfaces could reach lock screen controls.
Emergency exploit steps to try:
Access emergency dialer from lock screen
Look for camera access during emergency call
Check if contacts are accessible from emergency interface
Try accessing recent calls or call history
Look for notification panel access during emergency mode
Most of these exploits have been patched in recent Android updates, but they're worth attempting on older devices.
Pattern Lock Vulnerabilities
Pattern locks are still slightly easier to crack than PINs. If you can see finger smudges on the screen under good light, you might figure out the pattern. There are only so many ways to connect nine dots, after all.
Finger smudges on screens can reveal patterns under good lighting conditions or with powder dusting techniques, while the limited number of possible pattern combinations makes systematic attempts more feasible than PIN brute forcing. However, Android's increasing delays between failed attempts make this time-intensive and often impractical.
Pattern lock analysis shows that users typically create patterns using only 20 possible combinations before triggering extended lockout periods, with the system requiring users to wait increasingly longer periods between attempts.
Safe Mode Bypass
Safe mode used to bypass some third-party lock screens, but most people use the built-in Android lock screen now, so this rarely helps. Safe mode can bypass certain lock screen implementations by preventing third-party security apps from loading during boot.
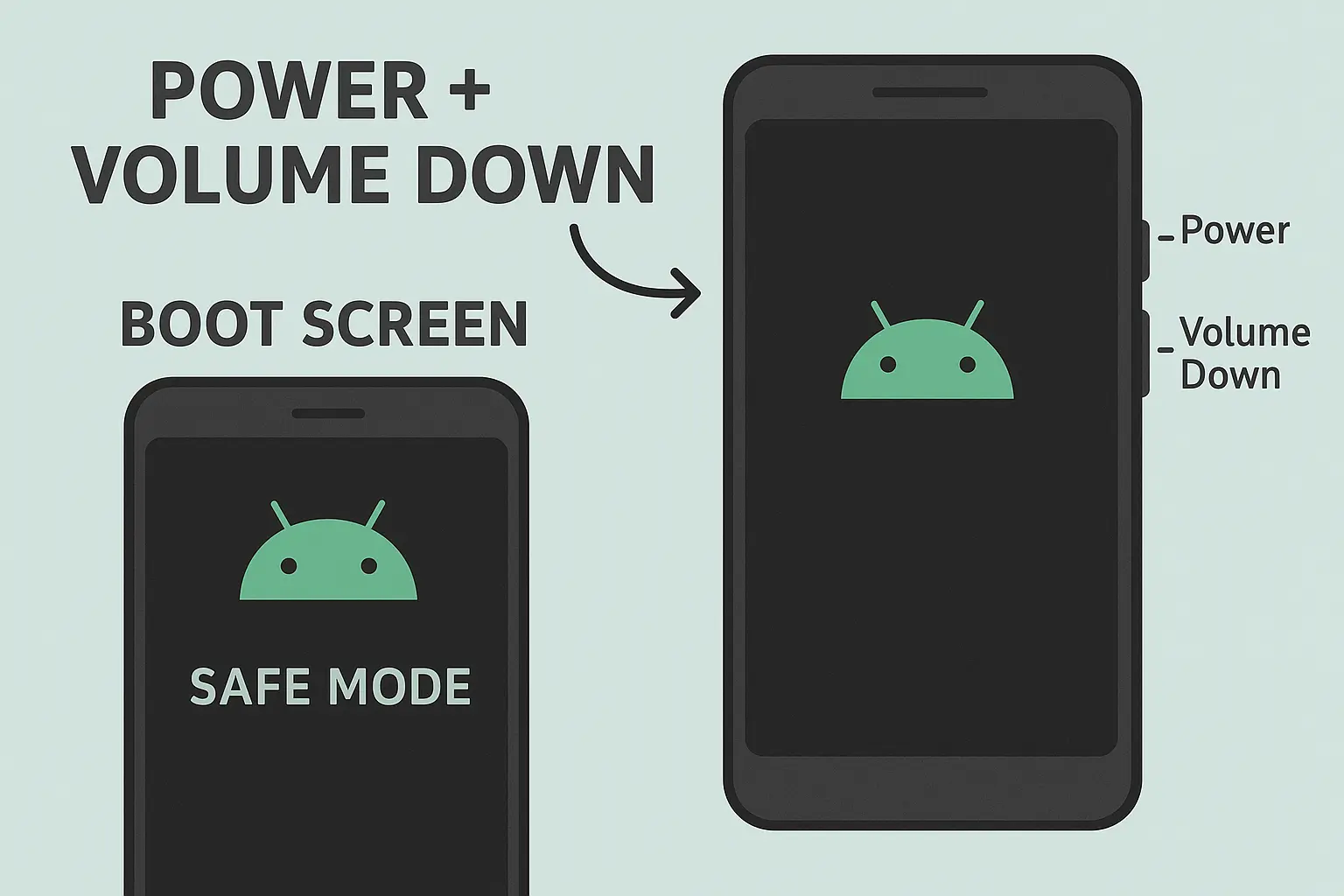
This method works by holding specific button combinations during startup and only affects devices using third-party lock screen applications rather than built-in Android security. Modern Android versions have largely eliminated these vulnerabilities through improved system integration.
Why Modern Phones Are So Hard to Crack
Here's the thing Google doesn't advertise but should: they've made Android incredibly secure. Your newer phone has a dedicated security chip that stores encryption keys completely separate from the main processor. Software can't touch it, which is why old-school bypass methods fail.
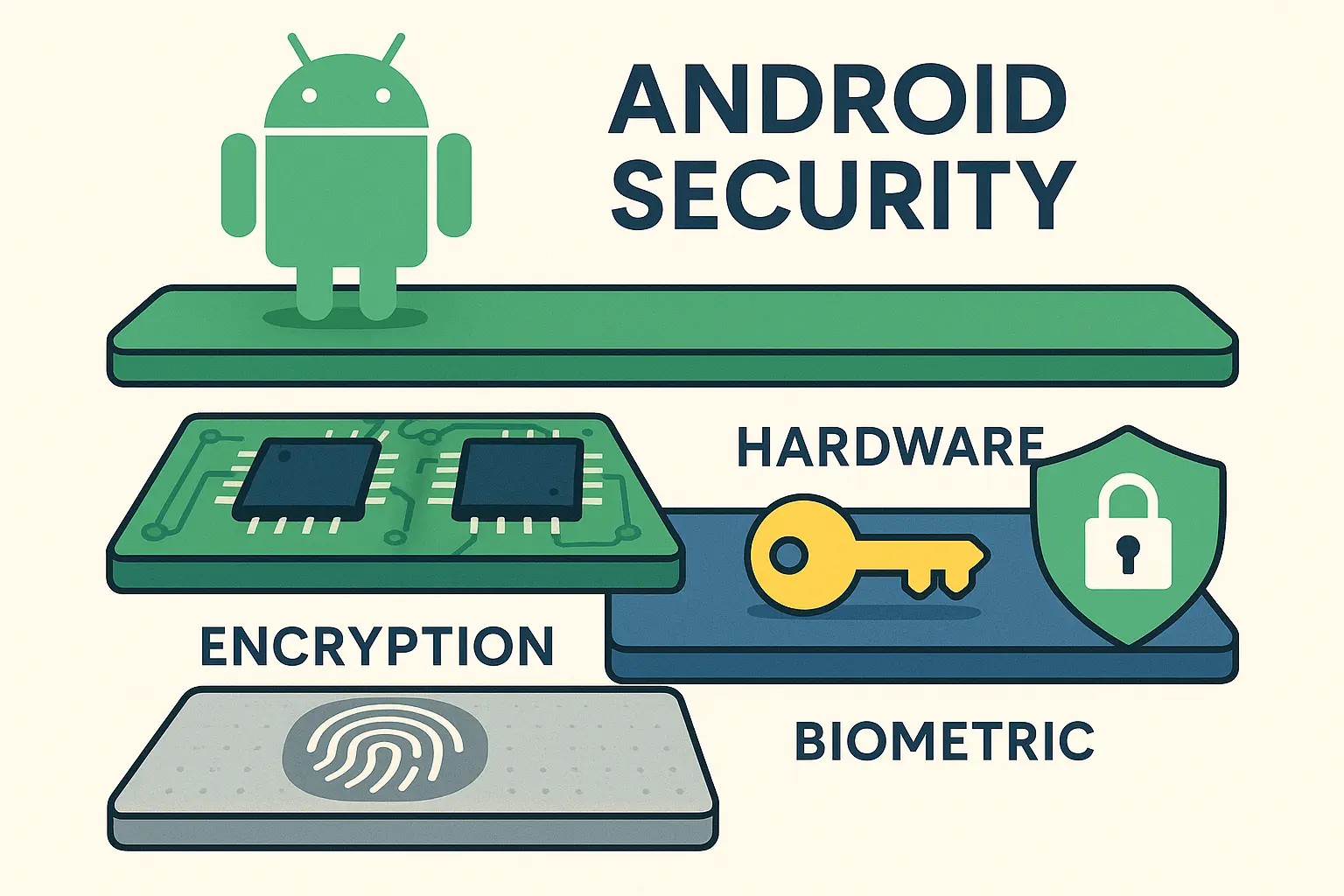
Hardware Security Evolution
Modern Android devices implement hardware security modules (HSMs) and Trusted Execution Environments (TEEs) that fundamentally change the security game. These dedicated security chips store encryption keys in hardware that software methods simply cannot access or modify.
This hardware-backed approach makes password bypass extremely difficult because the critical security components exist outside the reach of traditional software exploits. Your phone essentially has a separate computer dedicated solely to security functions.
Every Android update makes unauthorized access harder. The methods that worked on your old Galaxy S7 won't work on your current phone. This isn't a bug - it's intentional, and it's actually protecting you from real criminals who want your data.
Manufacturer Security Layers
Samsung adds their own Knox security on top of Android's protection. It's like having a security guard for your security guard. Great for keeping bad guys out, terrible when you're the one locked out.
Device manufacturers add their own security layers beyond Google's base Android protections. Samsung's Knox security platform and similar enterprise-grade systems monitor for tampering attempts and can permanently disable device functions if unauthorized access is detected.
When dealing with Samsung devices specifically, understanding their unique security implementations is crucial. Our comprehensive guide on Samsung phone accessories covers security features and compatibility considerations.
Locked bootloaders prevent custom recovery system installation, and unlocking them typically requires manufacturer authorization while triggering automatic factory resets.
Prevention for Next Time
The best unlock method is never getting locked out. I know, I know - super helpful advice after the fact. But for next time, here's what actually matters:
Set up Smart Lock while you can still get into your phone. Add your home as a trusted location, pair your smartwatch or car as a trusted device. Future you will thank current you.
Physical device protection plays a crucial role in preventing lockout scenarios caused by hardware damage. Consider investing in toughest phone cases that protect against drops and impacts that could damage biometric sensors or touchscreens.
Prevention setup that actually works:
Configure multiple unlock methods (PIN, pattern, biometric)
Enable Smart Lock trusted locations and devices
Set up Google account recovery options
Install and configure Find My Device
Create regular data backups to cloud storage
Use quality protective case to prevent damage
Test all unlock methods periodically
Rokform's military-grade cases provide the physical security that complements digital security measures, preventing the screen damage and hardware failures that often lead to password recovery situations. When first responders and military personnel trust Rokform's 6-foot drop protection and secure mounting systems, you know you're getting serious device protection.
For professionals who rely on their devices in demanding environments, choosing the right protection is essential. Our law enforcement phone cases provide the durability needed to prevent lockout situations caused by physical damage.
Make sure Find My Device is enabled and your Google account is logged in. This is your best bet for remote unlocking, but only if you set it up beforehand.
When to Accept the Factory Reset
Most people searching for unlock methods are going to end up factory resetting anyway. Modern Android security is just too good. The methods that worked five years ago have been patched, and the tools that work today mostly require setup you didn't do.
Your realistic options are:
Try Google's Find My Device if you set it up
Check if Smart Lock works (trusted places, devices, etc.)
Attempt ADB if you're technical and enabled debugging
Try a commercial tool if you have an older phone
Accept the factory reset and restore from backup
I wish I had better news, but Android security has evolved specifically to prevent the kind of access you're looking for. The same features that frustrate you right now are protecting your data from actual threats every day.
Understanding the evolution of phone security helps explain why prevention is better than recovery. Learn more about modern device protection in our guide to phone case materials and how they contribute to overall device security and longevity.
If none of the legitimate methods work, it's time to cut your losses. Factory reset, restore from your last backup, and set up better recovery options for next time. Sometimes the best solution is the one you don't want to hear.
The harsh reality? Most people discover these limitations only after they're already locked out. By then, your options have narrowed considerably, and the methods that promise easy solutions often deliver disappointment instead.
Understanding how to unlock android phone password without factory reset requires accepting that prevention beats recovery every time. The methods that worked five years ago have largely been patched, and the tools that work today might not work tomorrow.
Your best bet remains setting up multiple recovery options before you need them. Smart Lock configurations, Find My Device activation, and proper backup authentication methods will save you more headaches than any bypass technique ever could.
The bottom line is this: if you're reading this guide because you're currently locked out, try the Google methods first. They're your best shot at keeping your data intact. If those don't work and you have an older phone, maybe try a commercial tool or ADB if you're technically inclined. But be prepared for the reality that you might need to factory reset anyway.
Modern Android security isn't broken - it's working exactly as intended. The inconvenience you're experiencing right now is the price of having a phone that's actually secure against real threats. Next time, set up those recovery options while you still can access your device. Trust me on this one.









