Look, I get asked about iPhone viruses constantly. And honestly? The answer isn't as simple as "iPhones don't get viruses" - though that's technically true.
Here's what's actually happening: Your iPhone won't catch a traditional computer virus, but that doesn't mean it's bulletproof. Recent data shows that "the most commonly blocked attacks were scams (nearly 45%) and malvertising (nearly 42%)" according to Norton's Gen Threat Report for October to December 2024. So while your iPhone isn't going to get infected like your old Windows laptop, there are still real threats you should know about.
Let me break down what you actually need to worry about - and skip the fear-mongering.
Table of Contents
What Actually Threatens Your iPhone
When Your iPhone Is Acting Weird
How Bad Stuff Gets on Your Phone
How to Actually Protect Your Phone
What to Do When Things Go Wrong
Bottom Line
The Short Version
Traditional viruses? Not happening on iPhones
Scams, malicious apps, and phishing? Definitely possible
Jailbroken phones? All bets are off
Your best defense? Keep iOS updated and don't click sketchy links
Watch for warning signs like battery drain and overheating
If something's wrong, restart your phone and remove suspicious apps
What Actually Threatens Your iPhone
Forget everything you've heard about iPhone viruses. The real threats are much more boring - and much more common.

Can iPhones Actually Get Viruses?
Traditional computer viruses that copy themselves and spread? Nope, not happening on regular iPhones. Apple built iOS like a bunch of separate rooms - each app stays in its own space and can't mess with the others or your system files. It's like having roommates who can't get into each other's bedrooms.
This sandboxing system is why traditional viruses don't work on iPhones. They can't spread between apps or take over your whole system.
But here's the catch: If you jailbreak your phone, you're basically removing all the locks on those doors. Now everything can access everything, and you're vulnerable to the same malware that hits other devices.
The Stuff That Actually Happens
According to "with more than 7 billion smartphone users in the world" as reported by Surfshark, the scale of potential mobile security threats is massive. Here's what iPhone users actually face:
Real threats:
Fake apps that steal your login info
Phishing websites that look legit but aren't
Malicious ads that redirect you to scam sites
Sketchy configuration profiles that give hackers control
Spyware targeting specific individuals
Stuff that doesn't happen:
Self-replicating viruses
Malware that spreads between apps
System-wide infections (unless you jailbreak)
While exploring iPhone security concerns, it's worth noting that physical protection is equally important - learn more about comprehensive device protection in our guide to the best phone cases that complement your digital security measures.
Threat Type |
How Common |
What It Does |
How to Avoid It |
|---|---|---|---|
Phishing Attacks |
Very High |
Steals passwords and personal info |
Check URLs carefully, don't click suspicious links |
Malicious Apps |
Medium |
Harvests data, sends spam |
Read reviews, check app permissions |
Configuration Profiles |
Low |
Gives remote control of device |
Only install from trusted sources |
Advanced Spyware |
Very Low |
Complete device monitoring |
Keep iOS updated, avoid suspicious links |
When Your iPhone Is Acting Weird
Your phone will usually tell you something's wrong - you just need to know what to look for.
Red Flags That Something's Up
Performance issues:
Battery draining way faster than usual
Phone getting hot during normal use
Apps crashing more than normal
Everything running slower than it should
Network weirdness:
Data usage spiking for no reason
Friends saying they got weird messages from you
Unfamiliar network connections in your settings
Research from "expect about 10–20% battery loss per hour of screen time" according to McAfee. If you're seeing significantly higher battery drain during normal use, something's probably running in the background that shouldn't be.
Sarah noticed her iPhone 14 was getting unusually hot during light use and her battery was draining 30% faster than normal. After checking her battery usage in Settings, she discovered an unfamiliar app called "System Optimizer" consuming 40% of her battery despite her never opening it. She deleted the app and everything went back to normal.
That's it. If you notice these things, don't panic - but do investigate.
How Bad Stuff Gets on Your Phone
Most successful attacks don't exploit technical vulnerabilities - they exploit humans. Understanding how these attacks work helps you avoid them.
When App Store Apps Turn Bad
Apple's app review process isn't perfect. Sometimes apps with hidden malicious features slip through. Recent security research has identified several "Trojan-infected apps like SparkKitty have appeared, hiding in crypto wallets and fake TikTok clones to steal sensitive images" according to Safety Detectives.
These apps usually get caught and removed quickly, but they can cause damage before Apple notices.
The Human Factor
Most successful iPhone compromises happen because attackers trick users into:
Installing malicious configuration profiles
Entering credentials on fake websites
Downloading apps that look legitimate but aren't
Clicking links that lead to malicious sites
Advanced Attacks (Don't Worry About These)
Sophisticated attackers sometimes use previously unknown vulnerabilities to install spyware without user interaction. These zero-day exploits typically target government officials, journalists, or business executives - not regular users.
Most people don't need to worry about these advanced attacks, but understanding they exist helps put other threats in perspective.
How to Actually Protect Your Phone
Creating strong iPhone security isn't complicated. It's mostly about building good habits and using Apple's built-in protections properly.
Keep iOS Updated (This Is Huge)
iOS updates frequently contain critical security patches. Delaying updates leaves you exposed to known threats that Apple has already fixed.
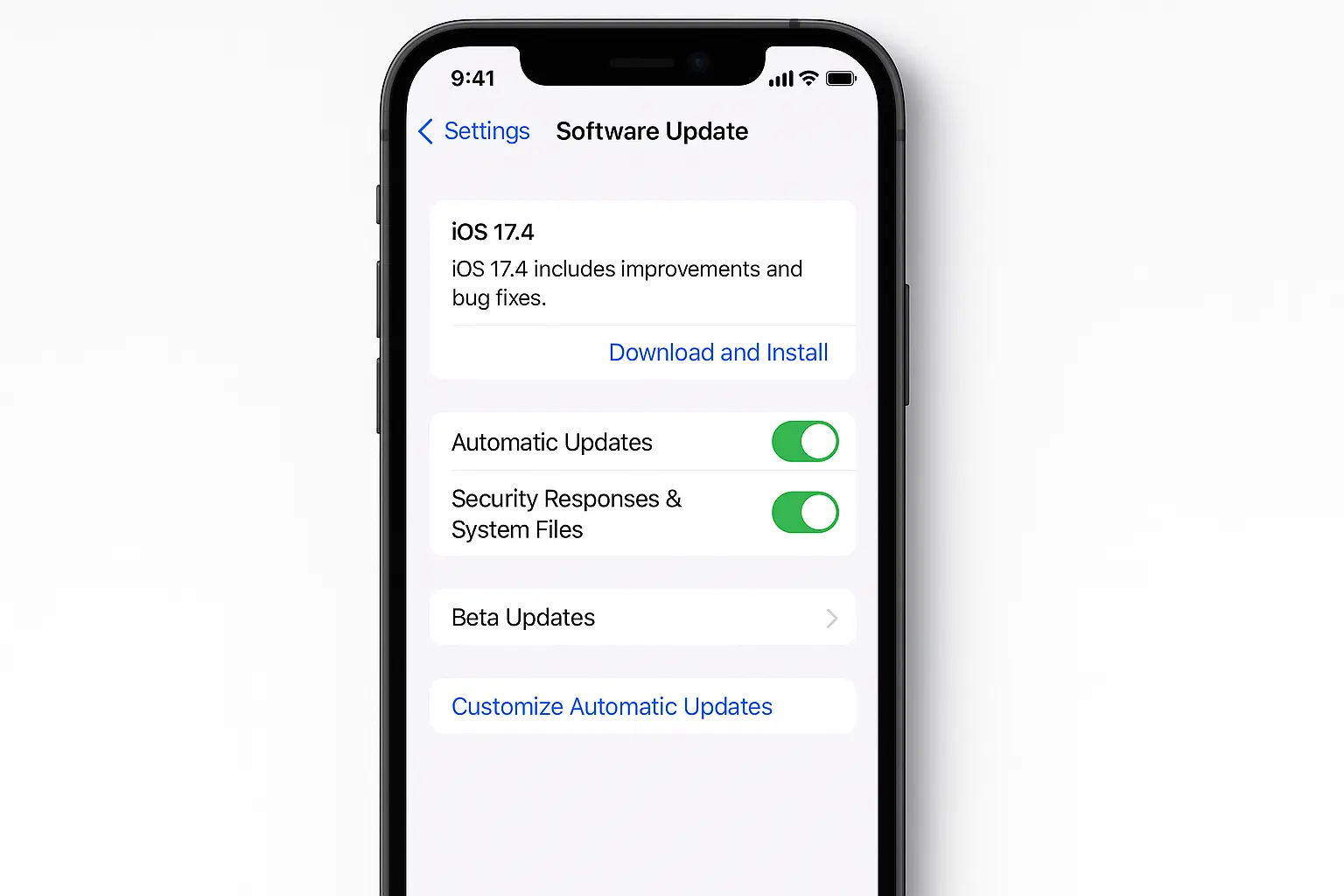
Set up automatic updates:
Go to Settings > General > Software Update
Tap "Automatic Updates"
Turn on both "Download iOS Updates" and "Install iOS Updates"
Done
Apple's Rapid Security Response feature delivers critical security fixes between regular updates. These appear as additional version numbers (16.4.1 (a)) and provide faster protection against urgent threats.
Smart App Store Habits
While the App Store is generally secure, following best practices provides extra protection.
Before downloading any app:
Read user reviews carefully
Check what permissions it requests
Make sure the permissions make sense for what the app does
Avoid apps with few reviews or sketchy permission requests
When downloading a photo editing app, Mark noticed it requested access to his contacts, microphone, and location - permissions that had nothing to do with photo editing. He checked the reviews and found users complaining about spam messages after installation. He chose a different app that only requested photo library access.
Managing app permissions:
Go to Settings > Privacy & Security and regularly review what apps have access to what. Many apps request more permissions than they need.
Permission Type |
Makes Sense For |
Red Flag For |
|---|---|---|
Camera |
Photo apps, video calls |
Flashlight apps, calculators |
Microphone |
Voice recorders, video apps |
Photo editors, simple games |
Location |
Maps, weather, ride-sharing |
Note-taking apps, flashlights |
Contacts |
Messaging, social media |
Single-player games, utilities |
Watch Out for Fake Apps
Be careful of apps that copy popular services with slightly different names, have poor grammar in descriptions, or request weird permissions. These fake apps often try to steal your login credentials.
Network Security Basics
Public Wi-Fi rules:
Avoid it for sensitive stuff when possible
Always verify network names with the business
Turn on "Ask to Join Networks" in Wi-Fi settings
Use cellular data instead when you can
Consider a VPN for public networks, but set it up through Settings > General > VPN & Device Management rather than relying only on VPN apps.

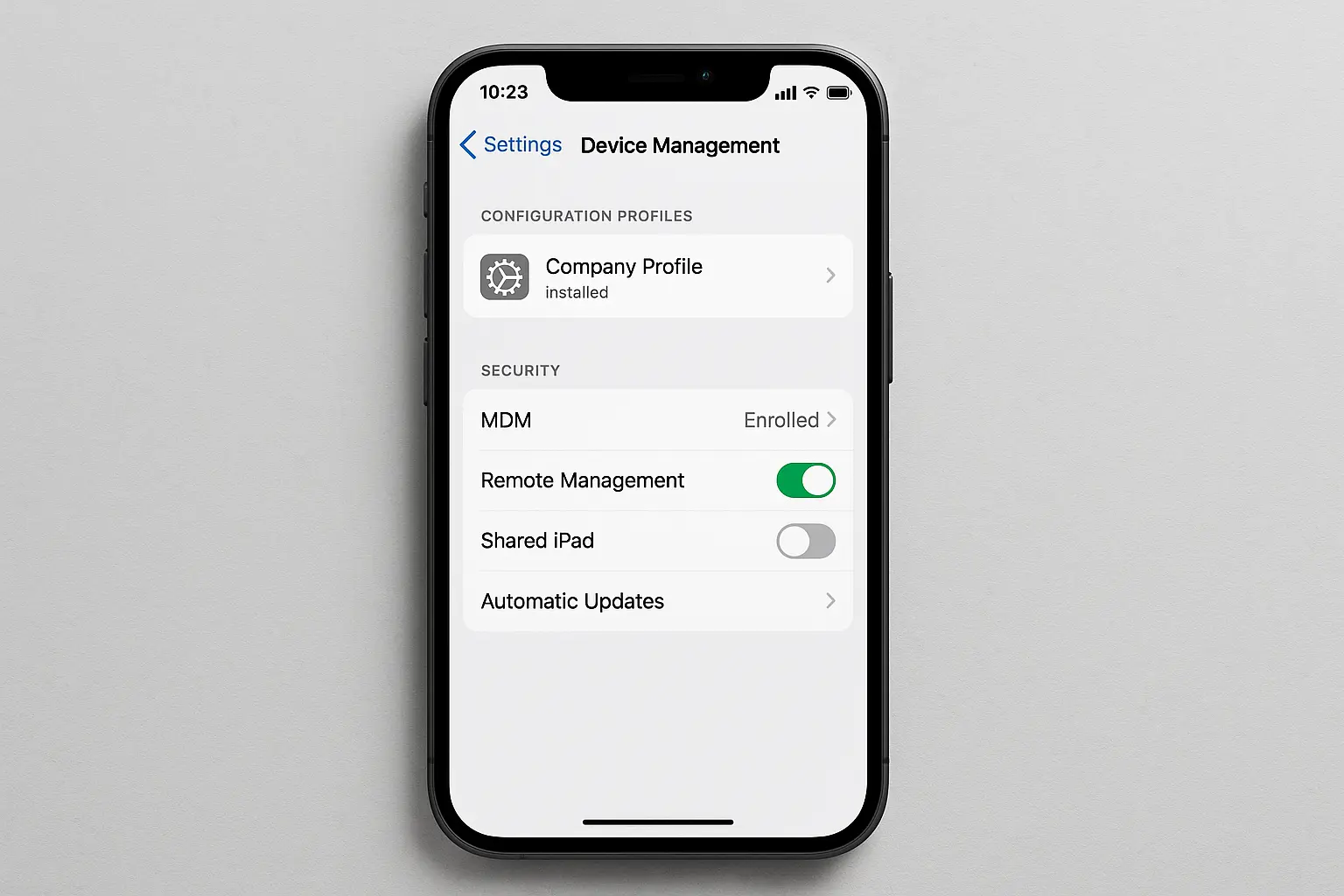
Configuration Profiles: The Sneaky Threat
Configuration profiles can give attackers administrative control over your device. Check Settings > General > VPN & Device Management > Configuration Profiles regularly.
Only install profiles from sources you absolutely trust. Be extremely suspicious of unsolicited requests to install profiles, even if they claim to be from legitimate organizations.
Backup Strategy
Enable iCloud Backup with two-factor authentication, but also create encrypted local backups through iTunes or Finder. Test your backups occasionally to make sure they actually work.
Security experts recommend regular backup testing, especially given that "smartphones play an integral part in our daily lives these days. They carry our personal information, financial details and our connection to the broader digital world" according to Panda Security.
What to Do When Things Go Wrong
When security incidents happen, having a clear plan minimizes damage and gets you back to normal quickly.

If You Think Something's Wrong
First, don't panic. Then:
Disconnect - Turn off Wi-Fi and cellular data
Restart your phone
Look for weird apps you didn't install and delete them
Clear Safari data - Settings > Safari > Clear History and Website Data
Check for malicious configuration profiles and remove them
Change your Apple ID password
Still having problems? Factory reset and restore from a backup
Most problems are solved by steps 1-4.
Tom's iPhone started showing persistent pop-ups and his friends reported receiving spam messages from his number. After disconnecting from networks and restarting his phone, he found an app called "Battery Saver Pro" that he didn't remember installing. He deleted it, cleared his Safari data, changed his Apple ID password, and the problems stopped completely.
During security incidents, physical protection becomes even more critical - explore our most protective phone cases to ensure your device remains secure during recovery.
When to Factory Reset
Sometimes you need to go nuclear. Factory reset is your best option when:
Performance issues persist after removing suspicious apps
You've confirmed sophisticated spyware is present
You installed apps from outside the App Store on a jailbroken device
According to "expect about 10–20% battery loss per hour of screen time" from Panda Security, if your device continues experiencing significantly higher battery drain after following removal steps, a factory reset may be necessary.

Fix Your Accounts Too
Compromised devices often lead to compromised accounts. After cleaning up your phone:
Change passwords for:
Your Apple ID
Email accounts
Banking apps
Social media accounts
Enable two-factor authentication wherever possible and review recent account activity for unauthorized access.

Monitor for hidden damage: Keep an eye on credit reports, bank statements, and account activity for several months. Some data theft doesn't show up immediately.
Bottom Line
Your iPhone is pretty secure, but it's not magic. The biggest threats aren't technical - they're people trying to trick you into giving up your info or installing something you shouldn't.
Stay updated, think before you click, and pay attention when your phone starts acting weird. That covers 99% of iPhone security.
While you're building these digital defenses, don't forget about physical protection. A cracked screen or damaged device can make your iPhone more vulnerable to both physical and digital threats. That's where quality protection comes in - providing drop protection that keeps your security features intact when life gets rough.
Your iPhone's security is only as strong as its weakest link. By combining smart digital habits with solid physical protection, you're creating comprehensive defense that keeps your device and data safe.
For complete device protection that complements your digital security strategy, explore our best iphone car dash mounts and best magnetic cases for iphone to ensure your device stays secure in every situation.









