My phone got snatched right out of my hands on a busy street corner in broad daylight. One second I was checking directions, the next I was standing there empty-handed, watching someone disappear into a crowd with my entire digital life.
That gut-punch moment taught me something important: the basic stuff we all do to protect our phones just isn't enough anymore. Thieves have gotten smarter, and honestly, most of us are walking around with targets in our pockets. According to Santander, phone theft is one of the most common types of crime: in London, a mobile is stolen every six minutes, according to police data.
What starts as a quick grab-and-run turns into a nightmare of compromised accounts, stolen identity, and financial headaches that can take months to sort out. I've spent years researching phone security after that experience, and I've learned that protecting your phone from theft requires way more than just being careful.
This guide covers everything from simple habit changes that cost nothing to advanced security systems that create multiple layers of protection. You'll discover techniques that security professionals actually use, learn how to set up systems that work even when your phone is gone, and understand exactly what to do in those critical first hours after theft.
Table of Contents
Physical Security: Your First Line of Defense
Digital Fortress: Configuring Your Phone's Built-In Protection
Next-Level Prevention: Smart Technology Solutions
When the Worst Happens: Recovery and Response Strategies
Final Thoughts
TL;DR
Front pockets beat back pockets every time - pickpockets can't access what they can't reach easily
Military-grade cases with secure mounting systems make opportunistic theft nearly impossible
Biometric locks combined with strong PINs create the perfect balance of security and convenience
Remote tracking and wipe capabilities only work if you set them up before you need them
Smart notification systems can alert you the moment someone tries to mess with your phone
The first hour after theft is critical - knowing exactly what to do can make or break recovery efforts
Insurance claims go smoother when you've documented everything beforehand
Physical Security: Your First Line of Defense
Here's something simple that makes a huge difference when learning how to protect your phone from theft: where you carry it matters way more than you think. I'm talking about real-world tactics that work in crowded subway cars, busy tourist areas, and anywhere else thieves like to operate.
After my phone got stolen, I started paying attention to how people carry their devices. The folks getting pickpocketed are almost always the ones with phones sticking out of back pockets or dangling from loose bag compartments. The goal isn't to turn you into a paranoid person who never uses their phone in public - we want to make your device an unattractive target while keeping it accessible for your daily needs.
Smart Carrying and Storage That Actually Works
Where you keep your phone directly impacts whether it stays in your possession. Small changes in your carrying habits can dramatically reduce theft risk without making your phone harder to access when you need it.
Pocket Strategy That Pickpockets Hate
Keep your phone in your front pocket. I know it sounds obvious, but think about it - when did you last feel someone brush against your front pocket? Probably never. Your back pocket? That happens all the time, and you barely notice.
Front pockets provide significantly better security because they're within your field of vision and require more deliberate movement to access. When you develop consistent carrying habits, maintaining awareness of your phone's location becomes second nature.
Security experts emphasize the importance of pocket placement, as noted by Santander's mobile security guide, which advises to "keep your device in your pocket, when possible, as thieves are looking for unlocked devices, which are more valuable than locked ones."
Consider avoiding easily accessible external pockets in crowded areas - this eliminates the most common theft opportunities. I learned this the hard way when someone lifted my phone from my backpack's side pocket while I was distracted looking at a map.
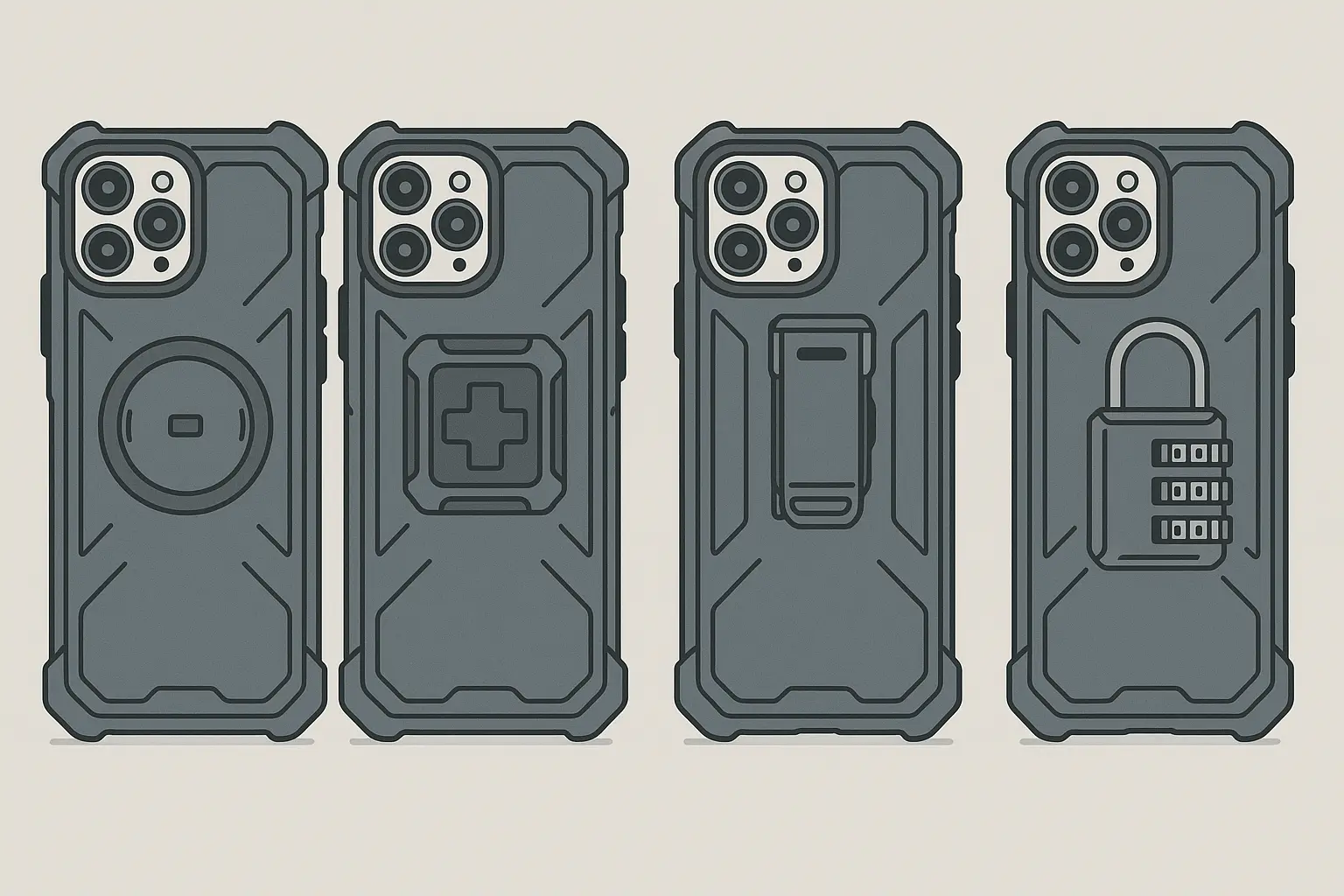
Military-Grade Cases That Mean Business
A really good case does two things: it protects your phone if you drop it, and it makes thieves think twice about grabbing it. I'm not talking about those flimsy plastic things - I mean cases that look like they could survive a small explosion.
Professional-grade protective cases offer dual benefits through secure mounting systems and robust construction. Cases with locking mechanisms and magnetic mounting capabilities allow you to secure your phone to surfaces while preventing easy removal. When someone sees a phone that's clearly built like a tank, they usually move on to easier targets.
When choosing protective equipment, consider reading our detailed comparison of the most protective phone cases to understand which features matter most for theft prevention and drop protection.
Reading the Room: Environmental Risk Assessment
Different environments present varying levels of theft risk. Understanding how to protect your phone from theft means adapting your security posture based on location and situation. I've learned to spot trouble before it starts, and it's saved me more than once.
Spotting High-Risk Zones Before Trouble Starts
Tourist areas, public transportation hubs, crowded events, and poorly lit locations consistently show higher theft rates. The combination of distracted targets and easy escape routes makes these areas particularly attractive to thieves.
Pay attention to your surroundings in these environments. Keep phones secured and avoid conspicuous usage that draws unwanted attention. It's not about being paranoid - it's about being smart.
High-Risk Environment |
Theft Risk Level |
Key Prevention Strategy |
|---|---|---|
Tourist Areas |
Very High |
Keep phone concealed, avoid flashy cases |
Public Transportation |
High |
Front pocket carry, maintain awareness |
Crowded Events |
High |
Secure zipped pockets, minimal phone use |
Parking Lots/Garages |
Medium-High |
Quick phone usage, stay near vehicle |
Restaurants/Cafes |
Medium |
Never leave unattended on table |
Shopping Centers |
Medium |
Secure bag compartments, stay alert |
Situational Awareness Without the Paranoia
Effective situational awareness involves maintaining peripheral awareness while using your phone in public. Position yourself strategically near walls or corners to limit potential approach angles, and always have a clear exit strategy when engaged with your device.
This isn't about living in fear - it's about developing smart habits that become automatic. I've trained myself to do quick environment scans before pulling out my phone, and it's prevented potential problems more than once.
Public Phone Use That Doesn't Scream "Rob Me"
Simple changes make a big impact. Prepare tasks beforehand and choose discrete cases. I always queue up my music, maps, or whatever I need before entering high-risk areas, so I'm not fumbling around with my phone when I should be paying attention to my surroundings.
Minimize phone exposure time in public through preparation. Use voice commands when possible, and avoid flashy accessories that advertise expensive devices.

Recovery-Focused Physical Prep Work
Physical modifications and preparations that enhance your ability to track and recover a stolen device create backup systems that work even when primary security measures fail. These preparations focus on making your phone easier to find rather than just harder to steal.
Hidden Tracking That Thieves Never See Coming
Discrete tracking devices hidden in phone cases or accessories provide backup location services that continue working even when thieves disable the phone's built-in tracking features. These secondary tracking systems often prove more reliable than phone-based solutions because they're harder to detect and disable.
For comprehensive tracking solutions, explore our guide on using AirTags with Android devices to understand cross-platform compatibility and setup options.
A business traveler places an AirTag inside their phone case's card slot, hidden behind their driver's license. When their phone is stolen from a hotel lobby, the built-in Find My iPhone is disabled within hours, but the hidden AirTag continues providing location updates for three days, ultimately leading to the device's recovery by local police.
The key is making these tracking devices invisible to casual inspection. Thieves often check for obvious tracking methods, but they rarely think to look inside case compartments or behind cards.
Digital Fortress: Configuring Your Phone's Built-In Protection
Okay, so you've got the physical stuff down. Now let's talk about turning your phone into a digital fortress. The crazy thing is, most phones already have incredible security features built in - but hardly anyone sets them up properly. I didn't either, until I had to learn the hard way.
Your phone's software settings create multiple layers of digital protection that can deter thieves and protect your data even after physical theft occurs. The catch? These features only work if you set them up correctly before you need them. I can't tell you how many people I've met who discovered their tracking was disabled or their backup wasn't working only after their phone got stolen.
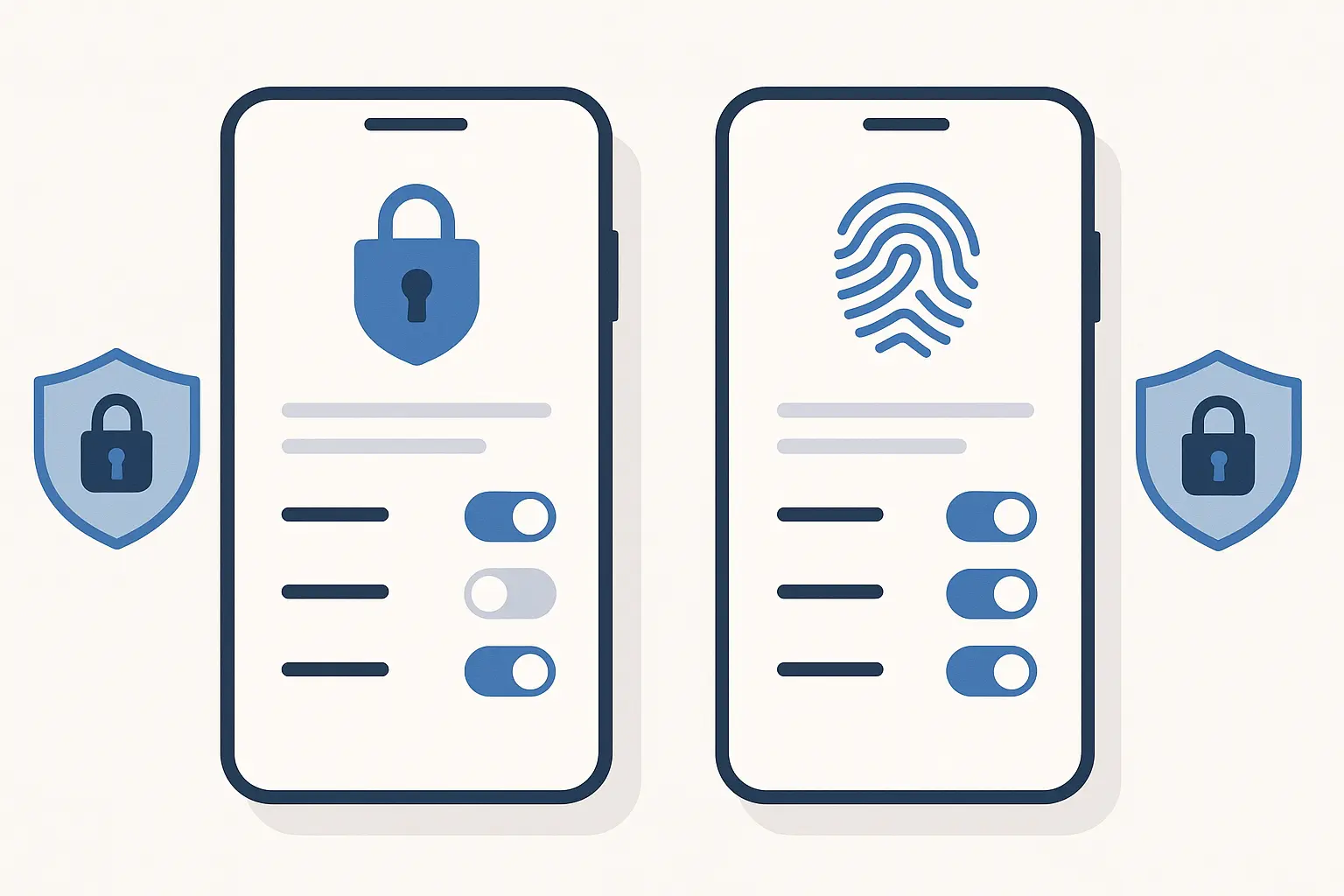
Lock Screens and Authentication That Actually Stop Thieves
Here's what I wish someone had told me about how to protect your phone from theft: don't just rely on one type of lock. Yeah, face unlock is convenient, but what happens when you're wearing sunglasses or it's dark? And fingerprint scanners get weird when your hands are wet or dirty.
Authentication systems serve as your primary digital barrier against unauthorized access. They need to balance security with usability to be effective in real-world situations.
Multi-Factor Authentication Done Right
Set up both biometric and PIN authentication, plus a PIN you can actually remember under stress. Trust me, when your phone gets stolen and you're trying to log into Find My iPhone from someone else's device, you don't want to be guessing your password.
Combining biometric authentication (fingerprint and face recognition) with strong PIN codes creates robust security that's still convenient for daily use. Set up multiple fingerprints and face profiles to ensure reliable access in different conditions.
Security experts recommend biometric authentication as noted by The Lab Repair, which states that "many smartphones also offer biometric security features, like fingerprint scanners or facial recognition, providing an extra layer of protection. Enabling these features can make it much harder for thieves to access your device if stolen."
Configure automatic lock timing to activate within 30 seconds. This prevents unauthorized access during brief separations from your device. I learned this lesson when I left my phone on a restaurant table for two minutes - that's all it took for someone to grab it and start trying to access my accounts.
Understanding your phone's security capabilities is crucial - check out our detailed analysis of IP67 vs IP68 ratings to learn about additional protection layers your device offers.
Emergency Access Without Security Compromises
Emergency contact information visible from the lock screen can help honest people return lost phones. Limit other displayed information that could be useful to thieves.
Configure medical ID access and emergency calling features to provide necessary functionality without compromising security. This creates a balance between accessibility and protection that works in real emergency situations.
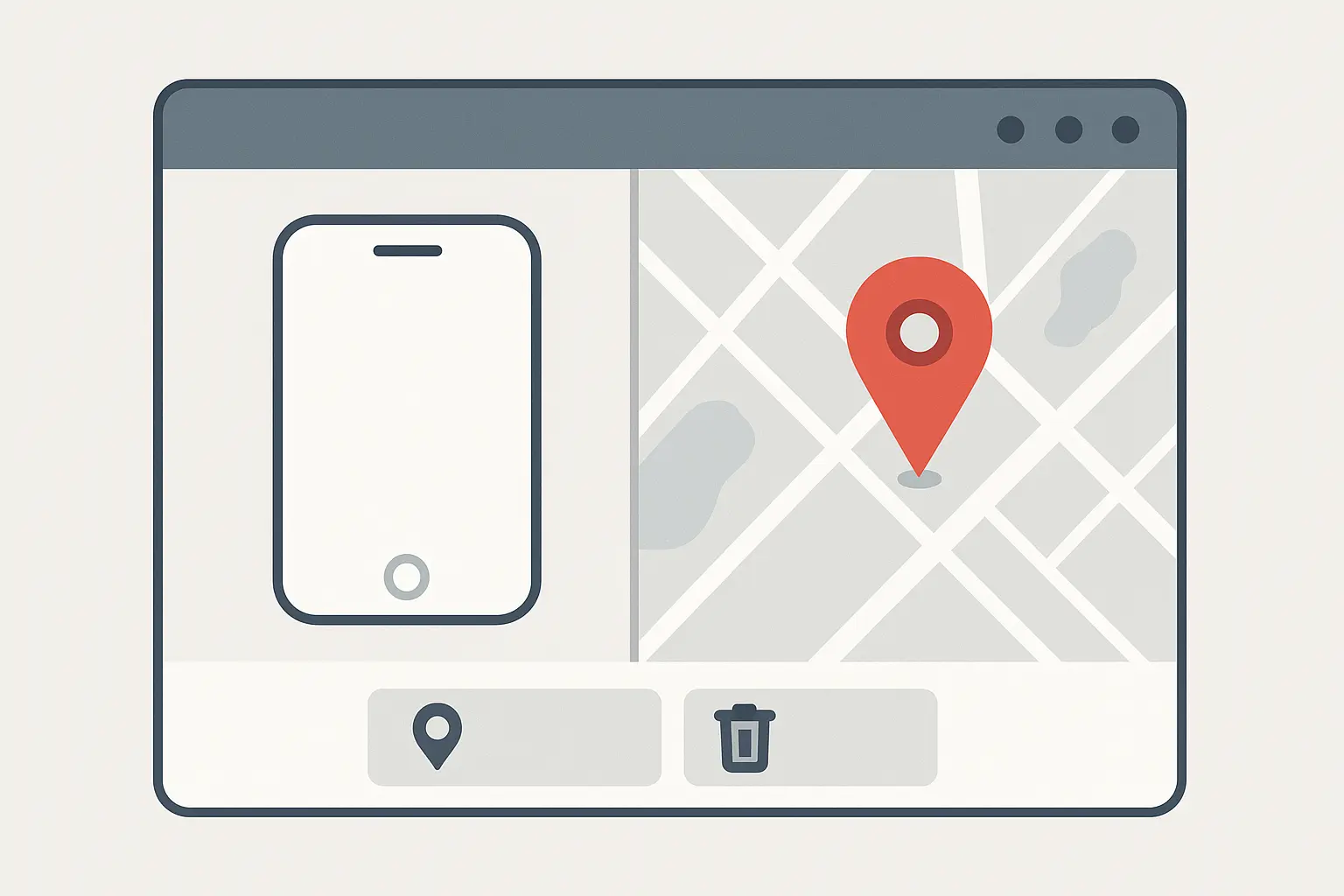
Remote Control When Your Phone Goes Rogue
This is where things get interesting - and where most people discover they're screwed. All those 'Find My Phone' features? They're useless if you never turned them on properly.
I spent an hour after my theft trying to track my phone, only to realize I'd never enabled offline finding. The thief had already turned it off, and my fancy tracking was worthless. Don't be me - test this stuff before you need it.
Find My Device Setup That Actually Finds Your Device
Location services, offline finding capabilities, and send last location features need to be enabled and tested regularly to ensure they function when needed. Configure trusted contacts who can help locate your device and set up automatic location sharing with family members.
According to The Lab Repair, "most smartphones come with built-in features that allow you to track and lock your device remotely. Use Find My iPhone for iPhones, and for Android, use Find My Device. These tools let you locate your phone on a map, lock it remotely, and even erase all data to ensure your personal information remains secure. Make sure these features are activated before your phone is ever stolen."
This creates a support network that can assist in recovery efforts. I've helped friends track down their stolen phones using family sharing features, and it's incredibly effective when set up properly.
Remote Wipe Capabilities Without the Data Loss Panic
Understanding how to remotely erase your device and practicing the process with old devices prepares you for emergency situations. Automatic data backup systems ensure that remote wiping doesn't result in permanent data loss.
Enterprise or family management systems provide additional remote control options that can be invaluable during theft situations. The peace of mind knowing you can completely wipe your device if needed makes the decision much easier when you're dealing with the stress of theft.
Next-Level Prevention: Smart Technology Solutions
Now we're getting into the really cool stuff - the kind of security that makes you feel like you're living in the future. This is about making your devices work together to watch each other's backs.
Advanced technology solutions go beyond basic security measures to create sophisticated theft prevention and recovery systems. These cutting-edge approaches leverage interconnected devices and intelligent monitoring to provide protection that adapts to your lifestyle and usage patterns.
My smartwatch now buzzes if my phone gets more than 30 feet away from me. Sounds paranoid? Maybe. But it's caught three situations where I would have walked away without my phone.
Smart Notifications That Work Like a Personal Security Guard
Intelligent alert systems provide immediate notification when your phone is moved, accessed, or tampered with without authorization. These systems act as an early warning network that can alert you to theft attempts before they succeed, giving you the opportunity to respond quickly.
Proximity Alerts That Keep You Connected
Apps that alert you when your phone moves beyond a set distance from paired devices create an invisible tether that prevents accidental loss and deters theft. Motion detection alerts during designated secure periods add another layer of monitoring that can catch unauthorized movement immediately.
The effectiveness of theft detection technology has been demonstrated in recent testing, as reported by Androi d Authority's theft detection analysis, which found that Android 15's new Theft Detection Lock feature "detects theft mainly by using the built-in accelerometer. If there's a sudden movement or change in direction, it's probable that someone grabbed the phone and ran off."
Unauthorized Access Detection That Catches Intruders
I've set up my phone to send alerts to my smartwatch and my wife's phone whenever someone tries to unlock it unsuccessfully more than three times. It's caught a few situations where someone found my phone and tried to get into it.
Alerts for failed unlock attempts, SIM card changes, and unusual account access patterns provide early warning of theft or tampering attempts. Notification systems that alert trusted contacts when suspicious activity is detected create a support network that can respond even when you can't.
For comprehensive security monitoring, learn more about managing iPhone notifications to optimize your alert system for maximum effectiveness.
Network Monitoring That Tracks Suspicious Activity
Monitoring for unusual network connections, unexpected location changes, or abnormal data usage patterns can indicate theft or unauthorized use. Carrier-based services that flag when your phone connects to towers in unexpected locations provide additional tracking capabilities that work independently of device-based systems.

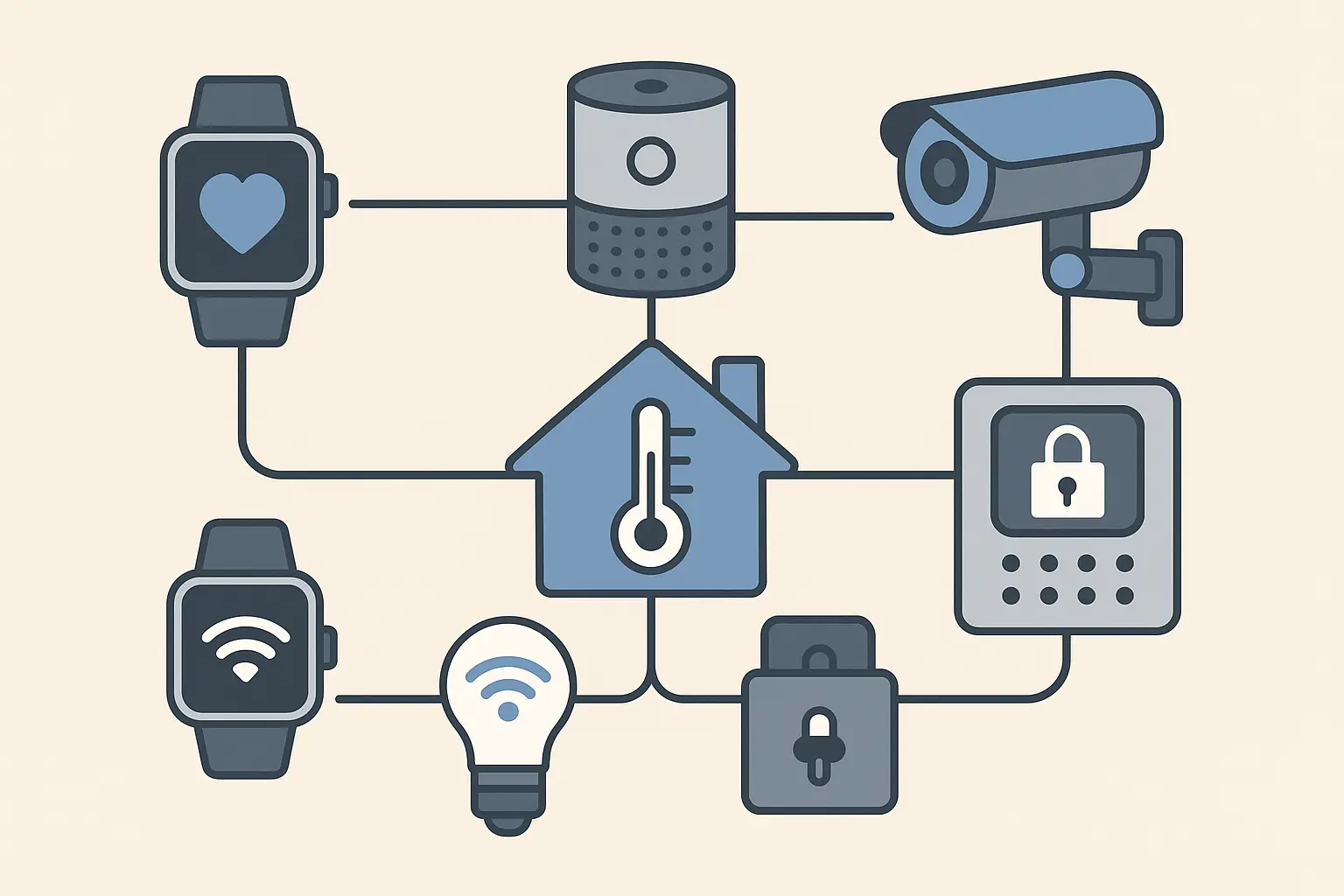
Connected Device Ecosystems That Work Together
Creating interconnected security systems that leverage multiple devices provides comprehensive theft protection and recovery capabilities. These integrated approaches use the power of connected devices to create redundant security layers that are greater than the sum of their parts.
Wearable Integration That Never Sleeps
Pairing your phone with smartwatches or fitness trackers enables alerts when devices become separated and automatic locking when connections are lost. Backup notification systems through connected devices ensure you stay informed even when your primary device is compromised.
Smart Home Security That Responds to Theft
Connecting your phone's security to home automation systems can trigger cameras, alarms, or lighting when theft is detected. This creates a comprehensive response that extends beyond just the stolen device.
Geofencing that automatically adjusts home security settings based on your phone's location and status adds another layer of integrated protection. When my phone's theft detection activates, my home security system automatically starts recording and sends alerts to my family members.
Security Integration |
Response Type |
Activation Trigger |
Recovery Benefit |
|---|---|---|---|
Smartwatch Alerts |
Immediate notification |
Phone disconnection |
Real-time awareness |
Home Security System |
Camera activation |
Theft detection |
Evidence gathering |
Car Integration |
Vehicle lock/alarm |
Phone separation |
Asset protection |
Family Tracking |
Contact notification |
Emergency mode |
Support network activation |
Cloud Backup |
Automatic sync |
Device compromise |
Data preservation |
Financial Apps |
Account freeze |
Suspicious access |
Financial protection |
When the Worst Happens: Recovery and Response Strategies
When your phone gets stolen, your brain goes into panic mode. You're angry, you're stressed, and you're probably not thinking clearly. This is exactly when you need a plan you can follow on autopilot.
Despite your best prevention efforts, theft can still occur. Having comprehensive response protocols maximizes recovery chances while protecting your personal information and accounts. The actions you take in the first hours and days after theft can determine whether you recover your device and how much damage the theft causes to your digital life.
The first hour is everything. After that, your chances of getting it back drop dramatically, and the damage to your accounts starts piling up. Here's your step-by-step playbook for when the worst happens.
Emergency Response: The Critical First Hour
Time-critical actions taken within the first hours after discovering theft can make the difference between recovery and permanent loss. These immediate response protocols focus on stopping ongoing damage while preserving evidence and recovery opportunities.
Your Emergency Contact Playbook
Immediately contact your carrier to suspend service. This prevents unauthorized usage charges and limits the thief's ability to access your accounts through SMS verification. Report the theft to local law enforcement with proper documentation - police report numbers and carrier reference numbers create an official record that's essential for insurance claims and recovery efforts.
Emergency Response Checklist:
Contact carrier to suspend service (within 15 minutes)
File police report with device details
Document IMEI and serial numbers
Activate Find My Device tracking
Alert bank and credit card companies
Change critical account passwords
Notify emergency contacts
Screenshot tracking information
Contact insurance provider
Secure backup devices
Account Lockdown That Stops Digital Theft in Its Tracks
Forget about your phone for a minute - your real problem is everything that phone can access. Banking apps, email, social media, work accounts - it's all sitting there behind whatever weak password you thought was good enough.
I watched my friend lose $2,000 because she didn't change her banking password fast enough. The thief got into her email, reset her bank password, and transferred money before she even realized what was happening. Don't let this be you.
Quickly changing passwords for critical accounts accessible through your phone prevents thieves from accessing your digital life. Start with email, banking, and social media accounts. Enable additional security measures on accounts and review recent access logs for suspicious activity to identify and stop unauthorized access before it causes serious damage.
Within 20 minutes of discovering her phone was stolen from a restaurant, Sarah used her laptop to change passwords for her email, banking, and social media accounts. She then remotely signed out of all active sessions and enabled two-factor authentication on accounts that didn't have it. When the thief attempted to access her accounts two hours later, they were locked out completely, preventing any financial damage or identity theft.

Long-Term Recovery: Playing the Long Game
Here's something nobody tells you about phone theft: the story doesn't end when you file the police report. Getting your phone back often takes weeks or months of persistent follow-up.
I know it's tempting to just buy a new phone and move on, but I've seen people get their devices back after two months because they stayed on top of it. Plus, there's something deeply satisfying about knowing the person who stole from you got caught.
Working with Law Enforcement Effectively
Providing comprehensive information to police including device serial numbers, IMEI codes, and tracking data gives them the tools they need for recovery efforts. Regular follow-up on case progress and providing new location information from tracking services keeps your case active.
Coordinating with multiple jurisdictions becomes necessary if the device moves between areas. I've seen cases where phones were recovered weeks later because the owner stayed in contact with police and provided updated tracking information.
Insurance Claims and Replacement Strategy
Navigating insurance claims processes efficiently requires proper documentation and understanding of coverage limitations. The payoff can be significant when done correctly. Plan for device replacement while continuing recovery efforts to ensure you're not left without a phone.
Implement enhanced security measures on new devices based on lessons learned to prevent repeat incidents. When selecting a replacement device, consider our comprehensive guide on the best phone cases to ensure your new device has maximum protection from day one.
How Rokform Solves Your Phone Security Problems
Look, I'm not going to pretend that one case solves everything, but after going through phone theft myself, I get why people invest in serious protection. Rokform's stuff is built like it expects trouble - which, let's be honest, is exactly what you want when you're carrying around a $1000+ device in sketchy areas.
Rokform's military-grade case systems and mounting solutions directly address the physical security challenges outlined throughout this guide. Their rugged polycarbonate cases provide 6-foot drop protection that keeps your phone functional even during theft attempts, while the patented RokLock™ system and industrial-grade MAGMAX™ magnets create secure mounting solutions that make opportunistic theft significantly more difficult.
The 360° protection system safeguards corners, cameras, and screens against both accidental damage and intentional tampering, while maintaining MagSafe® compatibility for wireless charging and magnetic accessories. For professionals working in high-risk environments, Rokform's accessory ecosystem - including wireless chargers, belt clips, wallets, and lanyards - creates multiple layers of physical security that address different theft prevention scenarios.
Ready to upgrade your phone's security? Check out Rokform's complete protection systems and find the perfect case for your device and lifestyle.
Explore our selection of the toughest phone cases designed specifically for high-risk environments and maximum theft deterrence.

Final Thoughts
Here's the bottom line: learning how to protect your phone from theft isn't about being paranoid or making your life harder. It's about being smarter than the people who want to take your stuff.
Most of this comes down to building better habits. Keep your phone in your front pocket. Set up tracking before you need it. Have a plan for when things go wrong. The boring stuff works, but only if you actually do it.
Protecting your phone from theft requires a multi-layered approach that combines physical security, digital configuration, advanced technology, and emergency preparedness. The strategies outlined in this guide work best when implemented together, creating overlapping layers of protection that make your device an unattractive target while ensuring you can recover quickly if theft does occur.
Remember that the best security system is one you'll actually use consistently. Choose the combination of measures that fits your lifestyle and risk tolerance, then make them part of your daily routine.
And if your phone does get stolen? Don't beat yourself up. It happens to careful people too. Focus on damage control, learn from what happened, and make sure your next phone is harder to steal and easier to find.
Most importantly, preparation beats reaction every time. Setting up these security measures before you need them ensures they'll work when it matters most. Take the time now to implement the strategies that make sense for your situation - your future self will thank you if the worst ever happens.
For additional security insights, read our analysis of phone cases that law enforcement professionals trust to understand what features matter most in high-stakes security situations.










