Your phone rings. The caller ID shows your bank's number. You answer, and they know your account balance. They're asking for your PIN to "verify your identity" due to suspicious activity.
Sounds legit, right? Wrong. You're about to become one of millions of spoofing victims.
Here's the scary truth: criminals can make any number appear on your caller ID. That "bank" calling? Could be someone in their basement halfway across the world. And your phone has no way to tell the difference.
According to the Federal Communications Commission (FCC), there were over 4.7 billion robocalls reported in 2023 alone, with a significant portion involving spoofed numbers. These attacks don't just bypass your phone's security - they bypass your common sense by exploiting our natural trust in familiar numbers.
I've spent years researching mobile security threats, and spoofing attacks keep getting scarier. What makes them so effective isn't just the technology - it's how they manipulate our instincts to trust familiar numbers and official-looking communications.
Table of Contents
Understanding the Real Threats Targeting Your Phone
Technical Defense Mechanisms That Actually Work
Behavioral Protection Strategies You Can Start Today
Emergency Response and Recovery When Things Go Wrong
TL;DR
Phone spoofing manipulates caller ID, network identifiers, and device information to deceive users and bypass security measures
Enable STIR/SHAKEN verification and configure built-in security features like "Silence Unknown Callers" for immediate protection
Always verify suspicious communications through independent channels - never respond directly to unexpected requests
Use authenticator apps instead of SMS-based verification for stronger two-factor authentication
If attacked, immediately change all passwords, enable additional security measures, and document everything for authorities
Long-term recovery requires credit monitoring, identity protection services, and comprehensive security upgrades
Understanding the Real Threats Targeting Your Phone
Phone spoofing represents one of today's most dangerous mobile security threats. Attackers manipulate caller ID information, impersonate cellular networks, and exploit human psychology to gain unauthorized access to your personal data and accounts. These attacks are particularly nasty because they appear to come from trusted sources like banks or government agencies.
The sophistication of modern attacks would shock most people. We're dealing with criminals who have access to the same technology that legitimate businesses use, but they're using it to deceive and steal from innocent victims.
How Modern Attacks Actually Work
Today's spoofing techniques exploit fundamental vulnerabilities in telecommunication protocols and mobile network infrastructure. Understanding these attack methods helps you recognize potential threats before they cause damage.
The Truth About Caller ID Manipulation
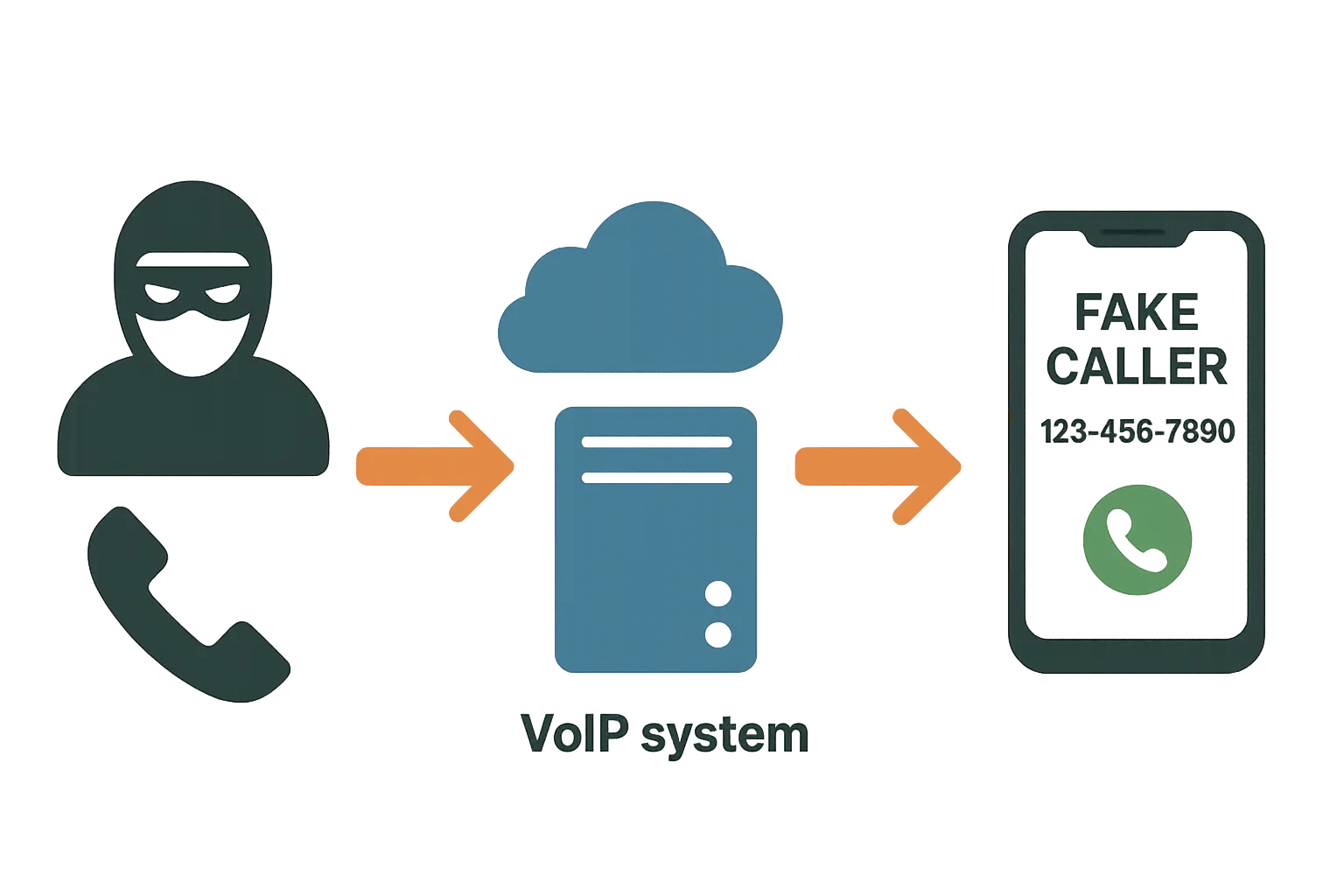
Here's the thing about caller ID: it's basically useless for security. Attackers use Voice over Internet Protocol (VoIP) services and specialized software to falsify caller ID information, making malicious calls appear to come from trusted institutions, government agencies, or even your own contacts.
Voice over Internet Protocol services have made caller ID manipulation accessible to virtually anyone with basic computer skills. Criminals purchase cheap VoIP accounts and use readily available software to input whatever phone number they want to display on your screen.
The scary part? Your phone has no way to verify that the displayed number actually matches the real caller. When you see your bank's number pop up, you naturally assume it's legitimate - but it could be someone sitting in their basement halfway across the world.
Take Sarah, a working mother who received a call displaying her bank's official number. The caller claimed suspicious activity had been detected on her account and requested her PIN to "verify her identity." Because the caller ID showed her actual bank's number and the caller knew her account balance, she provided the information. Within hours, $3,000 had been transferred from her account. The sophisticated manipulation made the scam nearly impossible to detect until it was too late.
Network Identity Manipulation: The Invisible Threat
Sophisticated attackers can create fake cellular towers and Wi-Fi networks that impersonate legitimate infrastructure, intercepting your communications and potentially installing malware on your device. These "man-in-the-middle" attacks are completely invisible to most users.
Fake base stations (sometimes called "stingrays" or "IMSI catchers") can be set up anywhere with relatively inexpensive equipment. Your phone automatically connects to the strongest signal, which means you might unknowingly connect to an attacker's fake tower instead of your carrier's legitimate one.
Once connected, everything you send and receive passes through their equipment first. They can intercept text messages, capture login credentials, and even push malicious software updates to your device. The worst part is that you'll never know it's happening - your phone works normally while they're stealing everything.
SMS and Message Manipulation Tactics
Text message manipulation allows criminals to send messages that appear to come from legitimate services, banks, or even your contacts, often containing malicious links or requests for sensitive information that can compromise your entire digital life.
SMS manipulation works similarly to caller ID tricks, but it's often more effective because people tend to trust text messages more than phone calls. Attackers can make messages appear to come from your bank, asking you to "verify" your account by clicking a link.
These messages often create a false sense of urgency - claiming your account will be closed or that suspicious activity has been detected. The links lead to fake websites that look identical to the real thing, designed to steal your login credentials.
Recent reports indicate that "scammers can make a call look like its coming from the bank, the police, or even your phone number" according to cybersecurity expert Caitlin Sarian, who documented a particularly disturbing case where attackers used a wife's phone number to call her husband claiming they had taken her hostage.
Social Engineering: The Human Element
Attacks become exponentially more dangerous when combined with social engineering tactics that manipulate human psychology and emotions. Attackers study their targets and craft convincing scenarios that bypass both technical security measures and common sense.
How Attackers Exploit Your Natural Trust
Criminals leverage the inherent trust people place in familiar phone numbers and official-looking communications to lower their guard and comply with fraudulent requests. They understand that most people want to be helpful and will often provide information when asked by someone who appears to be in authority.
Trust is both our greatest strength and our biggest vulnerability when it comes to phone security. We're hardwired to trust familiar numbers and official-sounding requests, especially when they come with a sense of urgency.
Attackers exploit this by doing their homework. They might research your social media profiles to learn about your bank, your employer, or recent life events. Then they craft their communications to reference specific details that make their requests seem legitimate.
Red Flag Indicator |
What It Looks Like |
Why It's Dangerous |
|---|---|---|
Urgent Action Required |
"Your account will be closed in 24 hours!" |
Creates panic that bypasses logical thinking |
Request for Sensitive Info |
Asking for passwords, PINs, or SSN |
Legitimate companies never ask for this via phone |
Unusual Communication Pattern |
Friend/colleague using formal language |
May indicate compromised account |
Pressure to Bypass Security |
"Don't call back, handle this now" |
Prevents verification through official channels |
Too-Good-To-Be-True Offers |
Unexpected prizes or refunds |
Designed to trigger greed response |
The Real Cost of Successful Attacks
The consequences of falling victim extend far beyond immediate financial loss, potentially affecting your personal privacy, professional reputation, and long-term digital security for years to come.
Financial Fraud: Beyond the Initial Loss
Communications often serve as entry points for elaborate financial fraud schemes that can result in unauthorized account access, fraudulent transactions, and identity theft that takes years and thousands of dollars to resolve completely.
The initial financial hit is just the beginning. Once attackers gain access to one account, they often use that information to compromise others. They might apply for credit cards in your name, take out loans, or even file fraudulent tax returns.
Recovery can take months or years. You'll spend countless hours on the phone with banks, credit agencies, and government offices trying to prove your identity and reverse fraudulent transactions. Many victims report that the stress and time investment is worse than the actual financial loss.
According to reports from the Federal Trade Commission, the United States experienced staggering losses amounting to approximately $1.5 billion from phone scams in 2023 alone.

Privacy Violations and Data Breaches
Successful attacks can lead to comprehensive data breaches where personal information, contacts, photos, and sensitive communications are compromised and potentially sold on dark web markets, creating long-term privacy and security risks.
Your phone contains an incredible amount of personal information - photos, messages, contacts, location history, and app data. When attackers gain access, they often extract everything they can find.
This information doesn't just disappear after the initial attack. It gets packaged and sold on dark web marketplaces, where other criminals can purchase it for future attacks. Your personal data might be used in identity theft schemes years after the original incident.
Professional and Personal Relationship Damage
When attackers gain access to your phone, they may impersonate you to contacts, colleagues, or family members, potentially damaging professional relationships and personal trust networks that can take years to rebuild.
Attackers don't just steal from you - they often use your compromised accounts to target your contacts. They might send messages to your coworkers asking for sensitive company information, or contact family members requesting emergency financial help.
These secondary attacks can destroy professional relationships and personal trust. Even after you explain what happened, some people remain suspicious. The damage to your reputation can last long after you've recovered from the initial attack.
Mark, a small business owner, fell victim to an attack that compromised his email and phone. The attackers used his accounts to contact clients requesting immediate payment transfers to a "new account due to banking issues." Three clients sent payments totaling $15,000 before Mark discovered the breach. Even after recovering the funds, two clients ended their business relationships, citing trust concerns. The incident cost Mark both money and valuable long-term business partnerships.
Technical Defense Mechanisms That Actually Work
Protecting yourself requires implementing multiple layers of technical defenses, from enabling built-in smartphone security features to configuring advanced authentication systems. These technical measures create barriers that make it significantly harder for attackers to successfully impersonate legitimate communications or gain unauthorized access to your accounts.

I've tested dozens of security configurations over the years, and I can tell you that most people are walking around with phones that have powerful protection features turned off. It's frustrating because these tools could prevent so many successful attacks.
Built-in Security Features You Should Enable Right Now
Modern smartphones include sophisticated anti-spoofing capabilities that provide substantial protection against common attack vectors when properly configured. Most people never enable these features because they don't know they exist or understand how to set them up correctly.
Your phone already has powerful security tools built in - you just need to turn them on. Manufacturers have been quietly adding anti-spoofing features over the past few years, but they're often buried in settings menus where most people never find them.
STIR/SHAKEN: Your First Line of Defense
STIR/SHAKEN verification systems cryptographically sign caller ID information to verify the authenticity of incoming calls and identify potentially manipulated numbers. This technology is available on most modern smartphones but requires proper configuration to be effective.
STIR/SHAKEN sounds complicated, but it's actually pretty straightforward. Think of it as a digital signature for phone calls - legitimate callers get a verified checkmark, while suspicious calls get flagged or blocked entirely.
Here's how to enable it:
Contact your carrier to confirm STIR/SHAKEN support (most major carriers offer it now)
On iPhone: Go to Settings > Phone > Silence Unknown Callers
On Android: Settings > Phone > Caller ID & Spam Protection
Enable automatic blocking of verified spam calls
The system isn't perfect, but it catches a significant percentage of manipulated calls before they reach you.
Advanced Call Filtering and Blocking
Configuring your phone's built-in call filtering systems creates additional barriers against unwanted communications while still allowing legitimate calls to reach you. These systems use machine learning and crowd-sourced data to identify suspicious calling patterns.
Most people only use basic call blocking, but modern phones offer much more sophisticated filtering options. You can set up rules that automatically handle different types of calls based on various criteria.
Advanced filtering options include:
Blocking calls from numbers outside your contacts
Sending unknown numbers directly to voicemail
Requiring callers to press a number to connect (stops robocalls)
Blocking calls from specific area codes or number patterns
Between January 2019 and September 2023, Americans lodged 2.04 million complaints about unwanted phone calls where people or robots falsely posed as government representatives, legitimate business entities, or people affiliated with them.
Multi-Factor Authentication: Your Security Lifeline
Implementing robust multi-factor authentication creates additional barriers that attacks must overcome to be successful. The key is using hardware-based authentication methods rather than SMS-based systems that are vulnerable to SIM swapping and manipulation.
Two-factor authentication is your best defense against account takeovers, but different types of 2FA offer varying levels of protection. SMS-based authentication can actually make you less secure if attackers have compromised your phone number.
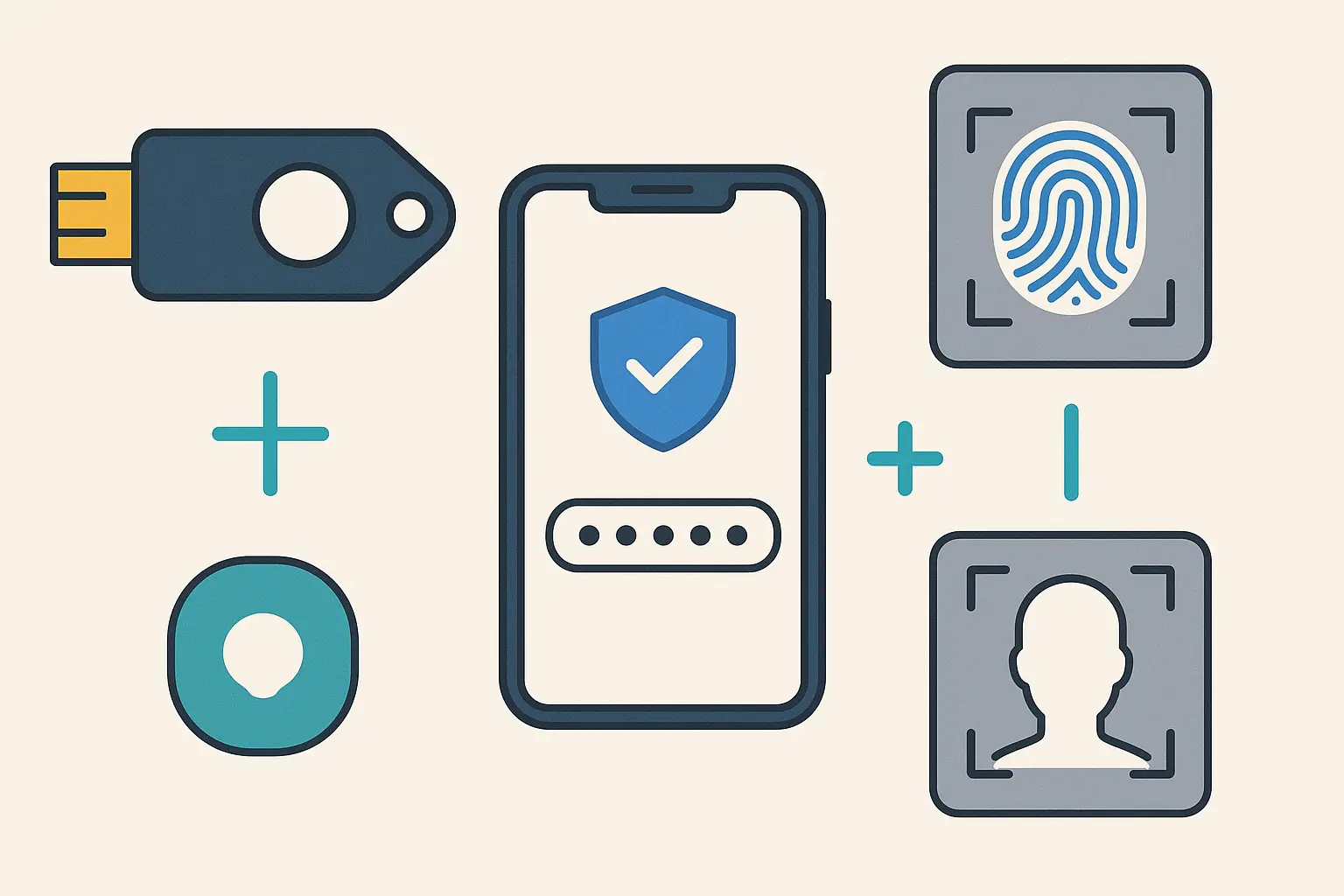
Hardware-Based Authentication That Works
Hardware security keys and authenticator apps provide much stronger protection than SMS-based verification because they generate codes locally on your device rather than relying on potentially compromised phone networks.
Authenticator apps such as Google Authenticator, Authy, or Microsoft Authenticator generate time-based codes that change every 30 seconds. Even if attackers intercept these codes, they're useless within minutes.
Implementation steps:
Download an authenticator app (I recommend Authy because it syncs across devices)
Enable 2FA on all critical accounts - banking, email, social media
Save backup codes in a secure location (somewhere other than your phone)
Consider hardware security keys for your most important accounts
Hardware keys such as YubiKey or Google Titan provide even stronger security because they require physical possession to authenticate.
Network Verification and VPN Protection
Configuring your device to verify network authenticity before connecting prevents connection to fake cellular towers or malicious Wi-Fi hotspots that could intercept your communications or install malware.
Your phone tries to be helpful by automatically connecting to networks, but this convenience creates security risks. Attackers can set up fake Wi-Fi hotspots with names such as "Free Airport WiFi" or "Starbucks Guest" to trick people into connecting.
Network security configuration:
Disable automatic connection to open Wi-Fi networks
Enable "Ask to Join Networks" on iPhone or "Network notification" on Android
Use a reputable VPN service when connecting to public networks
Monitor for unusual network behavior or unexpected disconnections
A good VPN encrypts all your internet traffic, making it useless to attackers even if they do intercept it.
Security Feature |
iPhone Location |
Android Location |
Protection Level |
|---|---|---|---|
STIR/SHAKEN |
Settings > Phone > Silence Unknown Callers |
Settings > Phone > Caller ID & Spam |
High |
Call Blocking |
Settings > Phone > Call Blocking & Identification |
Settings > Blocked Numbers |
Medium |
Network Security |
Settings > Wi-Fi > Ask to Join Networks |
Settings > Wi-Fi > Network Notification |
High |
App Permissions |
Settings > Privacy & Security |
Settings > Apps > Permissions |
Medium |
Automatic Updates |
Settings > General > Software Update |
Settings > System > System Update |
High |
Behavioral Protection Strategies You Can Start Today
Look, I get it. Reading about all these technical defenses can feel overwhelming. But here's the thing - some of the most effective protection doesn't require downloading anything or changing settings. It's about changing how you react when your phone rings or buzzes with a text.
Think of it this way: even if scammers get past all your technical defenses, they still have to convince *you* to hand over your information. And that's where you have all the power.

Building good security habits is harder than installing software, but they're often more effective at stopping attacks. I've seen people with top-tier technical security fall victim to simple social engineering because they didn't have the right behavioral defenses in place.
The Golden Rule: When in Doubt, Hang Up
Here's my personal rule that's saved me countless times: If someone calls asking for personal information, I hang up and call them back using a number I trust. Period. No exceptions.
I don't care if they claim to be from my bank, the IRS, or my own mother. If the request feels even slightly off, I end the call and verify through official channels. Real companies understand this approach - scammers hate it.
Your verification checklist:
Never give out passwords, PINs, or security codes over the phone
Don't click links in suspicious texts (even if they look official)
Look up contact info independently - don't use numbers from the suspicious message
When friends text asking for money or help, call them directly to confirm
Communication Verification: Your Personal Security Protocol
Establishing and consistently following verification procedures for unexpected communications can prevent successful social engineering attacks through spoofed channels. The key is developing automatic responses that don't rely on trusting the communication method itself.
Creating solid verification habits takes practice, but it becomes second nature once you establish a routine. The goal is to create automatic responses that kick in whenever you receive unexpected requests for information or action.
Independent Verification Methods That Work
Always verify suspicious communications through independent channels using different contact methods or official websites rather than responding directly to potentially spoofed messages or calls. This simple practice stops most attacks in their tracks.
Never trust the contact information provided in a suspicious communication. If someone claiming to be from your bank calls asking for account information, hang up and call the number on the back of your credit card instead.
Your verification process should include:
Never provide sensitive information through unsolicited communications
Look up official contact information independently (don't use numbers from the suspicious message)
Call back using verified numbers from official sources
Verify requests through multiple channels when possible
This might seem paranoid, but legitimate organizations understand security concerns and won't be offended if you verify their identity.
Recognizing Red Flags in Communications
After years of tracking these scams, certain patterns always pop up. Once you know what to look for, most attempts become obvious:
Urgency tactics: "Your account will be closed in 24 hours!" Real banks don't work this way.
Requests for sensitive info: No legitimate company asks for passwords or PINs over the phone. Ever.
Weird language from friends: If your normally casual friend suddenly texts in formal English asking for iTunes gift cards, that's not your friend.
Pressure to act fast: "Don't hang up, we need to handle this now." This is designed to prevent you from thinking clearly.
Trust your instincts. If something feels off about a communication, it probably is.
Jennifer received a text appearing to be from her credit card company stating: "URGENT: Suspicious activity detected. Click here to verify your account or it will be frozen in 2 hours." Instead of clicking, she noticed several red flags: the urgent timing, the generic greeting, and a slightly misspelled URL (amazom.com instead of amazon.com). She called her credit card company directly using the number on her card and confirmed no suspicious activity existed. This simple verification habit saved her from a sophisticated attack.
Privacy and Information Management
Controlling the availability of your personal information reduces the effectiveness of attacks by limiting the data attackers can use to make their deception convincing. This involves both digital privacy settings and being mindful about what information you share publicly.
Information is ammunition for attackers. The more they know about you, the more convincing their communications become. Reducing your digital footprint makes their job much harder.
Lock Down Your Social Media
Here's something most people don't realize: scammers research their targets on social media before attacking. Your posts tell them where you bank, work, and spend time. This helps them craft convincing messages.
I learned this the hard way when a client got scammed by someone who referenced her recent vacation photos and knew which gym she attended - all from her public Instagram.
Implementing strict privacy settings on social media platforms prevents attackers from gathering personal information that can be used to make communications more convincing and targeted to your specific situation.
Quick privacy wins:
Make all profiles private (yes, even LinkedIn)
Stop posting location check-ins in real-time
Remove personal details from your bio sections
Think twice before posting photos that show account numbers or personal documents
Consider doing a "privacy audit" of your social media accounts. Look at your profiles from the perspective of someone trying to scam you - what information could they use?
Contact Information Protection Strategies
Limiting the public availability of your phone numbers and contact information reduces targeting for attacks while still allowing legitimate contacts to reach you when needed.
Your phone number is often the key that unlocks everything else. Once attackers have it, they can use it for manipulation, SIM swapping, and social engineering against companies that use phone numbers for account verification.
Protection strategies:
Use separate numbers for public listings and personal use
Avoid sharing phone numbers on social media or public websites
Use email addresses instead of phone numbers for account recovery when possible
Consider using Google Voice or similar services for public-facing communications
Google Voice is particularly useful because it provides a buffer between your real number and the public. You can easily change or disable it if it becomes compromised.
Emergency Response and Recovery When Things Go Wrong
Despite your best efforts, attacks sometimes succeed. I've helped dozens of people recover from these incidents, and the first few hours are absolutely critical.
When attacks succeed despite your preventive measures, having a comprehensive response plan minimizes damage and facilitates rapid recovery of your security and normal operations. The first few hours after discovering an attack are critical for containing the damage and preventing further compromise of your accounts and personal information.
Time is your enemy when you've been hit. Every minute you wait gives attackers more opportunities to access additional accounts, make fraudulent transactions, or steal more of your personal information.
Immediate Response: Damage Control Mode
Stop the bleeding:
Change passwords on all important accounts (banking, email, social media)
Call your bank if financial info might be compromised
Enable two-factor authentication everywhere possible
Check recent account activity for suspicious transactions
The first hours after discovering an attack are critical for containing damage and preventing further compromise of accounts and personal information. Quick action can mean the difference between a minor inconvenience and a major financial disaster.
Account Security Lockdown Protocol
Immediately secure all potentially compromised accounts by changing passwords, enabling additional security measures, and reviewing recent activity for signs of unauthorized access. This rapid response can prevent attackers from causing additional damage.
Your lockdown procedure should be systematic and thorough:
Change passwords on all critical accounts immediately (start with banking and email)
Enable 2FA on any accounts that don't already have it
Review recent account activity and transactions for anything suspicious
Contact financial institutions if banking information may be compromised
Consider temporarily freezing credit reports with all three bureaus
Don't try to do this all at once - prioritize your most important accounts first, then work your way down the list.
Alerting Your Network: Damage Control Communications
Warn your network: Send a quick message to close contacts: "Hey, my phone/email was compromised. If you get weird messages from me asking for money or info, ignore them and call me directly."
Notify your personal and professional contacts about the potential compromise to prevent them from falling victim to secondary attacks using your identity. Quick communication can protect your relationships and prevent further damage to your reputation.
Attackers often use compromised accounts to target your contacts, so you need to warn people before they become victims too. Send alerts through channels you know are secure - if your phone was compromised, don't use it to send the warnings.
Your notification strategy should include:
Send alerts through verified channels (email from a secure computer, not the compromised phone)
Warn contacts about potential impersonation attempts
Provide alternative contact methods temporarily
Update social media with security warnings if appropriate
Be specific about what happened and what people should watch for. Generic warnings don't help much.
Documentation: Building Your Evidence File
Document everything: Take screenshots of suspicious messages before they disappear. Save call logs. Write down what happened while it's fresh in your memory. You'll need this for police reports and insurance claims.
Document all aspects of the attack for law enforcement reporting and insurance claims, including screenshots, call logs, and any financial impacts. Proper documentation can be crucial for recovering losses and prosecuting attackers.
Documentation might seem secondary when you're dealing with an active attack, but it's crucial for recovery and legal action. Many victims lose money because they can't prove what happened.
Your documentation process should include:
Screenshot all suspicious communications before they disappear
Save call logs and message histories
Document any financial losses or unauthorized transactions
Keep records of all recovery actions you take
Report to appropriate authorities (FTC, FBI IC3, local police)
Take photos of your phone screen if screenshots aren't working - you need some kind of visual evidence.

Long-term Recovery: Getting Your Life Back
Recovery isn't just about fixing immediate damage - you need to watch for delayed effects. Fraudulent accounts sometimes don't appear for months after the initial attack.
Complete recovery requires ongoing monitoring and enhanced security measures to prevent future incidents and detect any lingering compromise. This phase can take months or even years, depending on the extent of the damage.
Recovery is a marathon, not a sprint. Even after you've secured your immediate accounts and stopped the bleeding, you need to stay vigilant for months to catch any delayed consequences.
Credit and Identity Monitoring Systems
Set up monitoring:
Sign up for credit monitoring (many banks offer this free)
Check your credit reports quarterly
Set up account alerts for all financial accounts
Consider identity theft protection services
Implement comprehensive monitoring of credit reports, financial accounts, and identity usage to detect any ongoing fraud or misuse of compromised information. Many fraudulent activities don't show up immediately after the initial attack.
Identity theft often has a long tail - fraudulent accounts might not appear for weeks or months after the initial compromise. Monitoring services help you catch these delayed attacks before they cause major damage.
Monitoring implementation checklist:
Enroll in credit monitoring services (many banks offer free monitoring)
Set up account alerts for all financial accounts
Monitor identity theft protection services
Regularly check for unauthorized accounts opened in your name
Review credit reports from all three bureaus quarterly
Don't rely on just one monitoring service - different services catch different types of fraud.
Security Infrastructure Overhaul
Upgrade your security: Use this incident as motivation to build better habits:
Get a password manager and use unique passwords everywhere
Switch to app-based two-factor authentication instead of SMS
Install reputable security software on your devices
Create a plan for handling future incidents
Use the incident as an opportunity to comprehensively upgrade your personal cybersecurity infrastructure and practices. This investment in better security can prevent future attacks and give you peace of mind.
Getting hit by an attack is traumatic, but it's also an opportunity to build better security habits. Most people don't take security seriously until something bad happens - use this experience as motivation to do better.
Infrastructure improvements should include:
Implement a password manager with unique passwords for all accounts
Upgrade to hardware-based 2FA wherever possible
Install comprehensive mobile security software
Establish regular security audits of all accounts and devices
Create and test backup plans for future incidents
Think of this as an investment in your future peace of mind. Good security practices become habits that protect you for years to come.
The Bottom Line
Phone spoofing isn't going anywhere. If anything, these attacks are getting more sophisticated and harder to spot. But you're not helpless.
The scammers are counting on you to react emotionally - to panic when they say your account is compromised, or get excited about that "prize" you won. They want you to act first and think later.
Your best defense? Slow down. Question everything. Verify independently.

Protecting your phone from these attacks requires a combination of technical defenses, behavioral changes, and emergency preparedness. While the threat landscape continues to evolve, implementing these comprehensive security measures significantly reduces your risk and helps you respond effectively if an attack does succeed.
Remember that security is a process, not a destination. Attackers constantly develop new techniques, so you need to stay informed and adapt your defenses accordingly. The time you invest in protecting yourself now will pay dividends in avoided headaches, financial losses, and privacy violations down the road.
Start with the basics: enable your phone's built-in security features, set up proper two-factor authentication, and develop that verification habit. These simple steps will stop the vast majority of attacks before they can hurt you.
Remember, legitimate companies want you to be security-conscious. They won't be offended if you hang up and call back to verify. Scammers, on the other hand, will try to pressure you into staying on the line.
Trust your instincts. If something feels off, it probably is. Your gut reaction is often your best early warning system.
Stay safe out there.









