Here's something that'll keep you up at night: criminals can steal your phone number in minutes and drain your bank account before you even realize what happened. It's called SIM swapping, and it's way more common than you think.
According to a Hiya report, 9% of unknown calls in the final months of 2024 were fraud attempts. I've been researching phone security for years, and honestly? Most people are sitting ducks. But here's the good news - you don't need to be a tech expert to protect your phone number from hackers.
This guide shows you exactly how to lock down your phone number like Fort Knox. We're talking carrier security tricks they don't advertise, authentication methods that make you nearly impossible to target, and the digital cleanup that stops criminals before they even try.
Table of Contents
Warning Signs Your Number Is Under Attack
Understanding SIM Swapping (And Why It's So Scary)
Emergency Response: What to Do If You're Hit
Lock Down Your Carrier Account
Ditch SMS Authentication for Something Better
Clean Up Your Digital Footprint
Emerging Threats You Need to Know About
Your Action Plan
TL;DR
Call your carrier today - set up a 6-digit PIN that's not your birthday
Ask for "port freeze" protection (it's usually free but they won't offer unless you ask)
Ditch SMS codes - use an authenticator app or hardware security keys
Clean up your social media - criminals are watching for personal details
Set up multiple account recovery methods beyond just your phone number
Know the warning signs so you can act fast if you're targeted
Warning Signs Your Number Is Under Attack
Let's start with the scary stuff - how to tell if criminals are already targeting your phone number. Recognizing these red flags gives you a fighting chance to stop the attack before they drain your accounts.
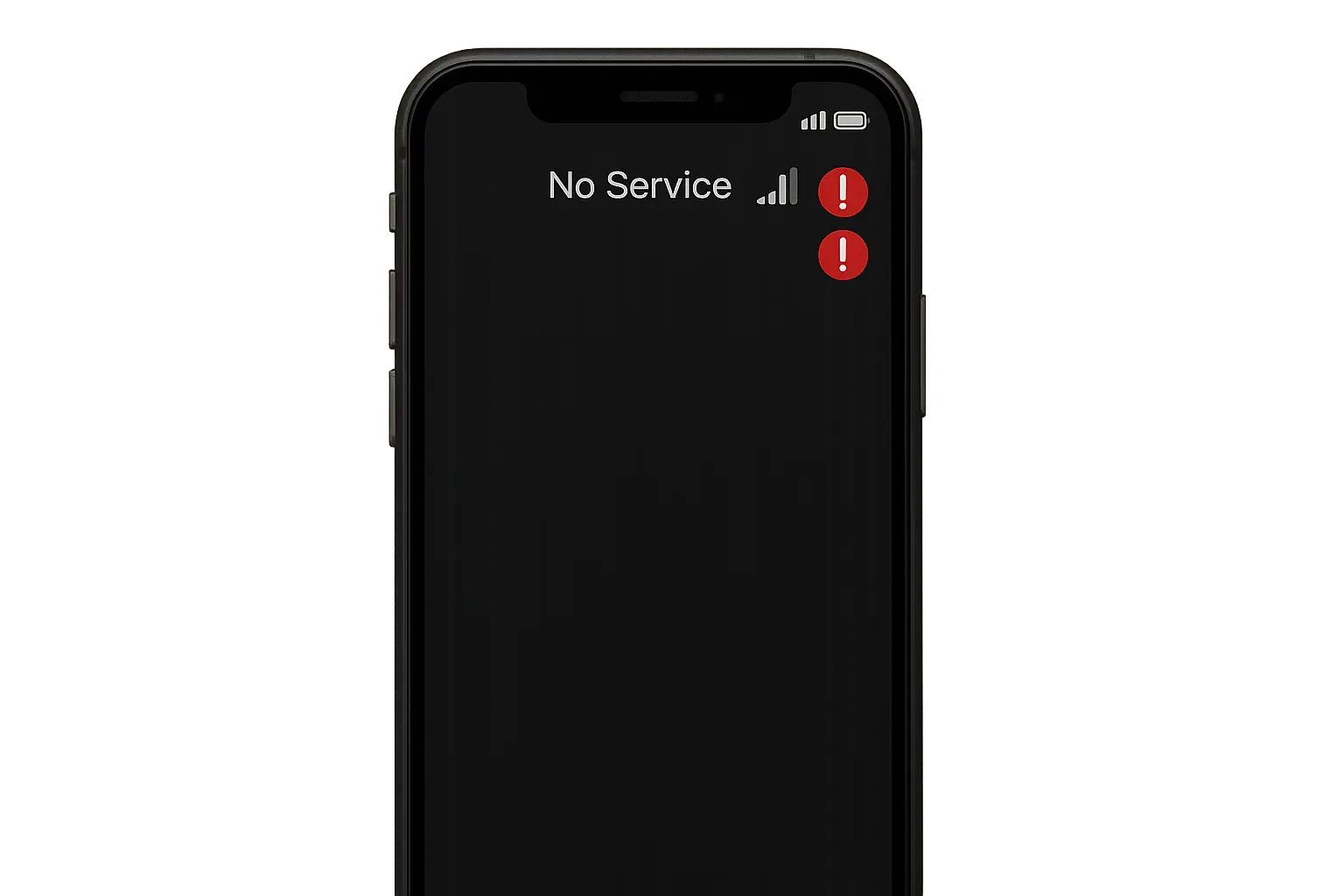
Your Phone Goes Dead (But Data Still Works)
Your biggest red flag? Your phone suddenly shows "No Service" or "SIM Not Detected" when nothing's wrong with your device. What's really scary is that your WiFi and data might still work fine - it's just calls and texts that stop working.
This disconnect happens because criminals have convinced your carrier to transfer your number to their SIM card. Your phone still connects to the internet, but all your calls and text messages are going to someone else's device.
Friends Say You're Sending Weird Messages
If people start telling you they got strange texts from your number, that's a massive red flag. Criminals often test their access by sending messages to your contacts or using your number to sign up for services.
You might also get notifications about your phone number being transferred to a new device, or suddenly can't receive verification codes from your bank or email providers.
Emergency Response: What to Do If You're Hit
If you suspect your phone number has been stolen, every minute counts. Here's your emergency playbook:
First 15 Minutes:
Call your carrier from any other phone (landline, friend's phone, work phone)
Report unauthorized SIM transfer immediately - don't troubleshoot your device
Demand they reverse the transfer and lock your account
While on hold, start changing passwords using WiFi (not your phone's data)
Next Hour:
Change passwords for email accounts first (this stops password resets)
Then banking and investment accounts
Then everything else
Document everything for police reports and insurance claims
Recent investigations show how organized these operations have become. "Phone theft is on the rise, especially in major cities like London, Paris, and New York. In February, the UK's Metropolitan Police said that phone theft in London is a business that generates £50 million ($67 million) per year" according to ZDNet.
Understanding SIM Swapping (And Why It's So Scary)
SIM swapping isn't about someone making expensive calls on your dime - it's about criminals completely hijacking your digital identity. When they steal your phone number, they become you in the digital world.

How These Attacks Actually Work
Here's what's terrifying: criminals don't need to be tech geniuses. They just need to convince your carrier's customer service rep that they're you and need to transfer your number to a new SIM card.
My neighbor lost $15K because her Instagram had her dog's name - the same name she used as a security question. The scammer called her carrier with her full name, address, phone number, and "Buddy" as verification. Twenty minutes later, they had her phone number and were resetting her passwords.
The Information They Already Have About You
What makes this so scary is how much personal info about you is already floating around online. Data breaches, social media profiles, public records - criminals piece together details about your Social Security number, previous addresses, and even your mother's maiden name.
Last month, a friend got a "bank verification" call. The caller knew her address, her dog's name from Instagram, and her mom's maiden name from a data breach. They sounded legit because they had real details about her life that only she should know.
How Fast They Can Destroy Your Life
Once criminals control your phone number, they move fast. Email accounts get hit in 15 minutes, bank accounts within 2 hours, and crypto wallets are cleaned out by morning. I've read reports of people losing their entire life savings - sometimes hundreds of thousands of dollars - while they slept.
Attack Stage |
What They Target |
How Long It Takes |
What You Could Lose |
|---|---|---|---|
Email Access |
Password resets, personal info |
15-30 minutes |
Control of all accounts |
Banking Phase |
Checking, savings, credit cards |
1-2 hours |
$10,000-$50,000 |
High-Value Targets |
Crypto, investment accounts |
2-4 hours |
$100,000+ |
Lock Down Your Carrier Account
Your mobile carrier offers security features that can stop SIM swapping cold, but they don't advertise them and most customers never ask. These are your first line of defense.
Set Up a Security PIN (Do This Today)
Call your carrier right now and set up a 6-digit PIN that's required for any account changes. Don't use your birthday, anniversary, or last four digits of your Social Security number - criminals often have this info.
Major carriers are finally taking this seriously. "T-Mobile allows customers to prevent SIM swaps and block unauthorized number port outs for free through their T-Mobile online account. Verizon has two security features called SIM Protection and Number Lock, which prevent SIM swaps and phone number transfers, respectively" reports TechCrunch.
Here's exactly what to do:
Call your carrier's customer service line
Say "I want to add a security PIN to prevent SIM swapping"
Choose a complex, unique 6-digit PIN
Ask for written confirmation
Test it by calling back and making sure they ask for the PIN

Enable Port Protection (It's Usually Free)
Ask your carrier for "port freeze" or "number lock" protection. This adds an extra verification step before your number can be transferred to another carrier or SIM card. Think of it as a deadbolt on your phone number.
Most carriers offer this for free, but they won't mention it unless you specifically ask. It's like they're hiding the good security features from customers who don't know to request them.
Ditch SMS Authentication for Something Better
SMS two-factor authentication is better than nothing, but it's exactly what SIM swappers are targeting. Time to upgrade to authentication methods that don't rely on your phone number.
Authenticator Apps Are Your Friend
Apps like Google Authenticator or Authy generate 6-digit codes that change every 30 seconds, and they work even if criminals steal your phone number. They're actually more convenient than SMS once you get used to them - no more waiting for text messages that might never arrive.
Steps to switch:
Download an authenticator app (Google Authenticator, Authy, or Microsoft Authenticator)
Go to your most important accounts (email, banking, social media)
Find "Security" or "Two-Factor Authentication" settings
Choose "Authenticator App" instead of "SMS"
Scan the QR code with your app
Save backup codes somewhere safe
Hardware Security Keys: The Ultimate Protection
Physical security keys (those little USB dongles) are the gold standard because criminals can't access them remotely. Even if they steal your phone number, they'd need the physical key to get into your accounts.
Tech executive Michael learned about hardware security keys after a colleague's crypto wallet got drained in a SIM swap. He bought two YubiKey devices - one for daily use and a backup in his safety deposit box. When he tried logging into Google from a new laptop, the system asked him to insert his key and press the button. No phone required.

How to set them up:
Buy FIDO2-compatible security keys from reputable manufacturers
Register them with your most critical accounts
Set up backup keys and store them securely
Gradually replace SMS 2FA across all supported services
Test regularly to make sure they work
Clean Up Your Digital Footprint
Protecting your phone number isn't just about technical security - it's about limiting the personal information criminals can use against you. Every detail you share online is potential ammunition for social engineering attacks.
Lock Down Your Social Media
Your social media profiles are goldmines for criminals. That innocent post about your childhood pet or high school graduation year could be exactly what they need to convince customer service they're you.
I've seen people post photos of their driver's licenses, passports, and credit cards on social media without thinking twice. Every piece of personal info you share makes their job easier.

Privacy settings audit:
Remove phone numbers, addresses, and family info from public view
Enable the strictest privacy settings on all platforms
Review tagged photos and posts from friends
Hide your friend/connection lists
Turn off location sharing and check-ins
Platform |
What to Lock Down |
Why It Matters |
|---|---|---|
Phone number, friend list, tagged photos |
High risk - lots of personal details |
|
Contact info, connection list |
Medium risk - professional info |
|
Account privacy, location tags, story visibility |
Medium risk - lifestyle patterns |
|
Twitter/X |
Phone number discovery, location services |
High risk - real-time info sharing |
Diversify Your Account Recovery Methods
Don't put all your eggs in one basket. If your only recovery method is your phone number and it gets compromised, you could be locked out of your own accounts.
When Jennifer's phone was stolen in Barcelona, she initially panicked about losing access to her work email and banking apps. But she'd set up her husband's phone as backup recovery and stored printed backup codes in her hotel safe. Within 30 minutes, she regained access to everything and remotely wiped her stolen device.

Set up multiple recovery options:
Add backup email addresses to important accounts
Set up security questions with answers only you'd know
Register trusted family members' phones as recovery options
Enable account recovery through authenticator apps
Download and securely store backup recovery codes
Emerging Threats You Need to Know About
Criminals are getting smarter, and new threats are emerging that make traditional phone number protection even more important.
AI Makes Social Engineering Scary Good
Artificial intelligence is making these attacks more convincing than ever. Criminals can now clone voices from just a few seconds of audio from your social media videos, generate fake documents, and automate the information-gathering process.
Voice cloning has reached the point where criminals can call your carrier sounding exactly like you. It's getting harder to tell what's real and what's AI-generated.
Smart Devices Create New Attack Vectors
Your smart doorbell might seem harmless, but it could reveal your daily schedule to criminals planning an attack. Connected fitness trackers expose location patterns and personal health information that can be used for social engineering.

These devices often contain personal information that criminals can use to sound more convincing when they call your carrier. Every connected device is a potential source of intel about your life.
Your Action Plan
Look, this stuff sounds complicated, but it's not. You don't need to implement everything at once. Pick three things from this list and do them today - your phone number is the key to your digital life, so treat it like it.
This Week:
☐ Call your carrier and set up a 6-digit security PIN
☐ Enable port freeze protection
☐ Download an authenticator app and set it up for your email
This Month:
☐ Replace SMS 2FA with authenticator apps on banking and social media
☐ Audit social media privacy settings
☐ Set up multiple account recovery methods
☐ Consider buying hardware security keys for your most important accounts
Ongoing:
☐ Regular privacy settings reviews
☐ Monitor for suspicious account activity
☐ Stay informed about new threats and protection methods

The threat is real and growing, but you're not powerless. Even basic protections make you a much harder target than someone with no security measures at all. Start with the carrier PIN and port protection - these two steps alone will stop most SIM swapping attempts.
Your future self will thank you for taking action before you become a victim. The best time to protect your phone number was yesterday. The second best time is right now.









